| CARVIEW |
ContrastAssess (IAST)
Secure every line of code with industry-leading accuracy.
Find and fix vulnerabilities that matter in your code.
Try Contrast
High false positives and limited real-time feedback lead to increased risk exposure
are patching vulnerabilities in a timely manner 1
waste time on vulnerabilities that pose minimal risk 2
days on average to fix an application security vulnerability 3
Contrast Assess identifies hidden application vulnerabilities by continuously analyzing code in real time for security risks
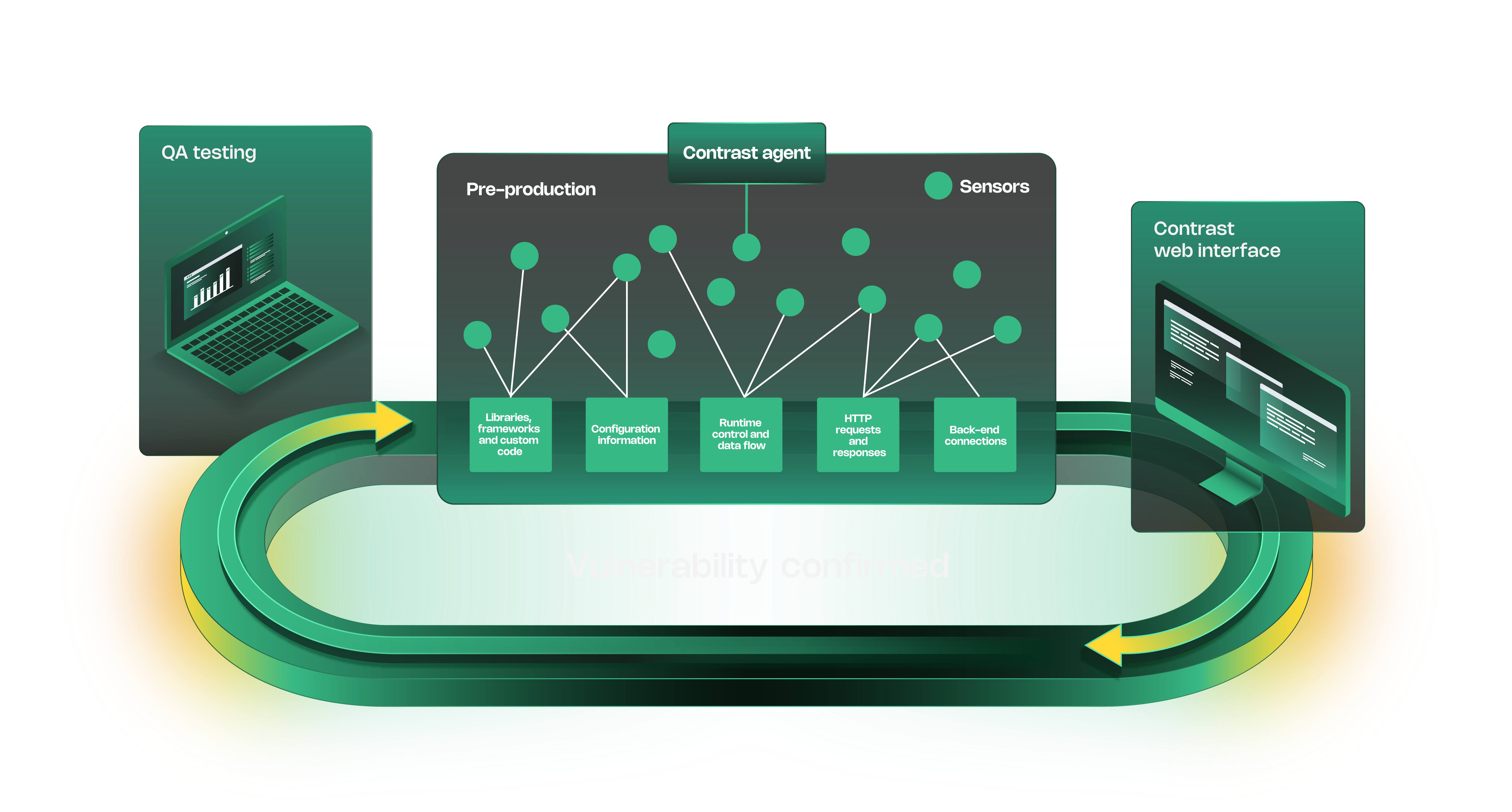
Eliminate deployment delays with proactive IAST that finds vulnerabilities earlier
Detect vulnerabilities early to prevent security breaches and exploits
Continuously monitor applications and APIs for real-time security assessments
- Detect vulnerabilities early to prevent security breaches and exploits
- Continuously monitor applications and APIs for real-time security assessments

Reduce manual effort with seamless security integrations and automation
Streamline compliance by integrating security into CI/CD pipelines
- Reduce manual effort with seamless security integrations and automation
- Streamline compliance by integrating security into CI/CD pipelines

Receive real-time guidance on security flaws and resolutions
Get actionable insights to remediate vulnerabilities efficiently
- Receive real-time guidance on security flaws and resolutions
- Get actionable insights to remediate vulnerabilities efficiently

Provide real-time insights to mitigate risks during development
-
Secure every line of code
Detects and prioritizes vulnerabilities and guides teams on how to eliminate security risks.
-
Live architecture and flow view
In-depth visualization of application components, code trees and data flow.
-
Remediation guidance
Pinpoints exactly where a vulnerability appears in code, and how it works.
-
Visualize application architectural components
Identifies vulnerabilities to form a starting point for threat modeling remediation.
-
Application attack intelligence
Provides a mapping of software routes that are executed during the testing.
-
Continuous runtime vulnerability detection
Instantly identifies risks in running applications without scanning delays.
-
Seamless DevSecOps integration
Embeds security into development workflows for proactive threat mitigation.
-
Vulnerability explanation
Enables developers to fix vulnerabilities easily without the need of security expertise.

Defend your applications and APIs with Contrast One™
Managed runtime security powered by the people who built it.
Learn more
Customers Recommend
FAQ
-
Contrast Assess uses an agent that instruments the running application with sensors. These sensors continuously monitor the application's code execution, data flow, and configuration in real time as it is executed. This Interactive Application Security Testing (IAST) approach, which combines static and dynamic analysis from within the application, pinpoints actual vulnerable, exploitable lines of code, drastically reducing false positives compared to standalone SAST or DAST.
-
Contrast Assess is designed for both developers and AppSec teams, streamlining the DevSecOps workflow. Developers receive immediate, actionable security feedback that pinpoints vulnerable lines of code and remediation guidance directly within their IDE, test or QA environments as they code, making security a continuous part of development. AppSec teams benefit from a centralized view of high-fidelity results, which eliminates the need to manually sift through false positives.
-
Contrast Assess can identify a broad range of vulnerabilities in custom code, open-source libraries, frameworks and application configurations. This includes common risks like SQL injection, Cross-Site Scripting (XSS), insecure configurations and others detailed in the OWASP Top Ten list. It also pinpoints the vulnerable lines of code and the full data flow path, making remediation faster.
-
Contrast Assess integrates with the platform's Software Composition Analysis (SCA) capability to identify third-party libraries and their known vulnerabilities. Crucially, it provides runtime context to determine if a vulnerable method in a library is actually being called and used by the running application, allowing teams to prioritize remediation efforts based on true, active risk.


