| CARVIEW |
Navigation Menu
-
Notifications
You must be signed in to change notification settings - Fork 1.6k
Releases: ory/hydra
v25.4.0
v25.4.0 brings first-class support for agentic authorization with the Device Authorization Grant (RFC 8628) and OAuth 2.1 discovery endpoint, making it easier for agents, IoT devices, and headless clients to obtain and manage access securely. Combined with new consent-chain revocation and migration fixes for CockroachDB v25+, Hydra v25.4 strengthens its role as the web and AI scale-ready OAuth 2.1 and OpenID Connect server for modern applications.
Ory has moved to a new versioning scheme. Read about our new version scheme. Interested in self-hosting Ory with support, SLAs, and advanced features? Check out our offerings.
Highlights
Agentic authentication use cases
This release makes Ory Hydra a stronger foundation for agentic authentication, where autonomous agents or constrained devices need to obtain and manage access without a full browser or direct human interaction. Two key updates enable this:
- Device authorization grant (RFC 8628): Essential for headless or limited-input clients (e.g., smart TVs, IoT devices, AI agents). It allows users to securely authorize agents through a secondary device, solving a common gap in agentic workflows.
- OAuth 2.1 discovery endpoint: Hydra now serves both OpenID Connect and OAuth 2.1 discovery documents, aligning with emerging standards. This simplifies integration for agents that expect OAuth 2.1 metadata and removes friction in federated or automated flows.
Together, these features address longstanding issues for agentic use cases by combining standards compliance with Hydra’s production-grade session and consent handling.
Device authorization grant (RFC 8628)
Adds full device flow support for devices without a browser or with limited input (smart TVs, consoles, agents).
Revoke token chains by consent challenge ID
New capability to revoke the entire token chain (refresh token and all derived access tokens) produced by a specific consent session.
OAuth 2.1 discovery endpoint
Hydra now serves /.well-known/oauth-authorization-server in addition to /.well-known/openid-configuration to aid OAuth 2.1 and certain integrations (per RFC 8414).
Improvements
- Lower latency when revoking linked Kratos sessions by making revocation asynchronous.
- Client updates with JWKS URI: PATCH/PUT no longer blocked when
json_web_keys_uriis set (andjson_web_keyspresent). - JWT query performance: added an index for faster JWT-related lookups.
- CLI: clearer usage/help examples.
Fixes
- CockroachDB v25+ migrations: corrected/updated migration scripts; includes device-flow down/auto-commit fixes.
- Postgres UUIDs: use
uuid_generate_v4()instead of MD5-based generation (enable theuuid-osspextension if not already). - Case-insensitive
user_codescrubbing in device flow. - Validation:
tos_urivalidation corrected. - Docs: fixed JWT access token documentation link.
Security and dependencies
- go-jose v3.0.4 with a backport for CVE-2025-27144.
- Go toolchain upgrades (1.24.x) and crypto stack updates (e.g.,
ThalesGroup/crypto11,circl) addressing advisories. - General dependency hygiene and CI hardening.
Upgrade notes
- Run migrations before rolling out v2.4.0.
- CockroachDB users on v25+: this release includes specific migration fixes; ensure your migration runner picks up the updated scripts.
- Postgres users: ensure
uuid-osspis enabled (CREATE EXTENSION IF NOT EXISTS "uuid-ossp";) to support native UUIDs.
- Device flow UI: add the two required screens/routes in your login/consent app to use RFC 8628.
- Monitoring: if you scrape Prometheus on public endpoints, expect additional metrics.
Auto-generated release notes
Bug Fixes
-
Add repo syncing for polis (46d17f8):
-
Add virtual expiry column to flow for easy cross-db querying (1c402e3):
-
Allow updating when JWKS URI is set (#3935) (#3946) (fb1655b):
The client validator no longer rejects PATCH and PUT updates when
JSONWebKeysURIis non-empty andJSONWebKeysis not nil. -
Always use EC private keys in tests (7481827):
-
Better tracing in proxy HTTP (0d8a797):
-
changelog-oel: Cap grace period for refresh token rotation at 30d (35d5d58):
-
changelog-oel: Reduce rows read when checking past consents (ace80c2):
-
changelog-oel: Replace
returning *with defined column names (0b26e27): -
changelog-oel: Update expires_at on token use (0588744):
-
changelog-oel: Use keyset pagination instead of offset (cbf14c0):
-
Copybara script (7b33358):
-
Correct multiple instances of 'stragegy' typo (#3906) (50eefbc):
This commit addresses several occurrences where 'strategy' was
misspelled as 'stragegy' throughout the codebase.Additionally, a similar issue was found and corrected in the Ory
documentation repository (ory/docs), with a corresponding pull request
submitted. -
Deduplicate down migrations (02baf36):
-
deps: Update go-x (582a3c5):
-
Escape IPv6 regex string (0ba326a):
-
Failing CI in OSS repos (c900985):
-
Fix expires_at timestamp not in UTC leading to local test failures (337000a):
-
Fixed typo in description of api (4551eb6):
-
Force autocommit for device auth code migration (#3991) (29761f4), closes #1234 #1234:
-
Force SQL operator precedence in pagination v2 to ensure nid isolation (43c9be1):
-
Hydra CI (dde63d8):
-
Hydra tracing (38ee050):
-
hydra: Instrument metrics also on public endpoints (8aee364):
-
hydra: Use prometheus metrics instead of SQA metrics (7a6592e):
-
Identity queries (a30f021):
-
Ignore flaky keys in Hydra HSM tests (469b2ad):
-
Ignore non SQL files when applying migrations (38a28d4):
-
Implicit transactions for cockroach v23.5 and simplified migration logic (fbc982a):
-
Include go.mod in vendored oryx (08a3ab4):
-
Increase refresh token grace period (50608c2):
-
infrastructure: Hydra oss CI (e846541):
-
Jsonx.ApplyJSONPatch (c6fa2a6):
-
JWT documentation link to point to the correct resource (#3907) (b746e41):
The previous link in the documentation led to a page unrelated to JWT.
Updated the URL to https://www.ory.sh/docs/oauth2-oidc/jwt-access-token,
which provides proper JWT guidance. -
Migration problems (fe459ea):
-
Migrations on Cockr...
Assets 44
- sha256:62db9fee0ad35fa408c921f60c8f525546d498bab0e531090bc8f7201f2b54942.66 KB
2025-11-07T14:57:00Z - sha256:54e7f076302de80b3300aa7d3e7e3f413f2e6b93af3cd1aeec04cd80a49bf8f696 Bytes
2025-11-07T14:57:00Z - sha256:24f4b6c4a26f20176adcb127823044a4aa12416eb43508aaedc546b431afb34f13.6 MB
2025-11-07T14:56:58Z - sha256:1a11af3c0825d03674a0c3b4254ea9d0ee07ae88b95fcf2e2a914d31ee97ee2314.3 MB
2025-11-07T14:56:59Z - sha256:d7b41750314052e7df915e973f8c155cd1118c00da3ad7daa9f5e3f1c39dd4a513.1 MB
2025-11-07T14:56:58Z - sha256:581aa0541815190856f1903b56a9e98dc836fdcf101c6707c26ab088b1f8f57413.5 MB
2025-11-07T14:56:58Z - sha256:62a0d946b9291f97d6870c7be6aec27f5068a63cc1407bf68f98697dc7bd8df913.5 MB
2025-11-07T14:56:58Z - sha256:51e058f8573f0f15cb1cdda9966b4af78478388797ffb4a0794c448849b0598315.2 MB
2025-11-07T14:56:55Z - sha256:62af62b2921ef6b6a95f647c30bbd536fe0a2215f3d1adbe4d8bae67b0c62a5013.9 MB
2025-11-07T14:56:55Z - sha256:41c75db98ba1a6e3810c00f2ee0d48731a51bb10d29318ef0e5310ba7933695f14.3 MB
2025-11-07T14:56:53Z -
2025-11-07T14:19:27Z -
2025-11-07T14:19:27Z - Loading
v2.3.0
We’re thrilled to announce the release of Ory Hydra 2.3.0! This version comes packed with graceful token refresh, performance improvements, and fixes that enhance stability, reduce database load, and streamline the developer experience. We strongly recommend upgrading to take advantage of these enhancements and ensure the best possible OAuth2 and OpenID Connect experience with Ory Hydra. Thank you to everyone who contributed!
Ory Hydra now supports graceful refresh token rotation, making OAuth2 and OpenID Connect refresh flows significantly more resilient in scenarios such as Single Page Apps and IoT. Even in highly distributed or concurrent environments, Hydra gracefully handles token refreshes reliably, ensuring tokens are not dropped or double-used.
Previously, the redirect_uri was not required when performing flows with scope=openid. This release enforces the requirement to comply with the OpenID Connect standard.
PR: #3900
Hydra now supports explicit SQL migration commands migrate sql up|down|status that streamline database schema management and help with zero-downtime upgrades.
PR: #3894
- Access token strategy & advanced CLI improvements
The CLI introduces new parameters and an option to specify a custom client ID on creation, making it easier to manage and script Hydra deployments.
PRs: #3718, #3725, #3874 - Built-in login & consent UI for
hydra perform authorization-code
A minimal built-in UI for login and consent can be enabled when testing with the CLI, removing the need to spin up a separate service.
PR: #3845
Unused indices have been removed, down migration scripts renamed for consistency, and all migrations are more efficient overall.
-
Improve persistence logic – Database transactions and concurrency have been improved across the authorization and token handlers.
PRs: #3756, #3763, #3886 -
Support for more claims in password grant – You can now include additional claims in the password grant flow, providing extra flexibility in advanced scenarios. Only available with an Ory Enterprise License.
PR: #3864 -
Transaction Wrappers
Authorization and token issuance are now wrapped more consistently to prevent partial writes and race conditions.
PRs: #3730, #3763 -
Improved Docker setup
Docker configurations have been refined, removing inconsistencies in the Compose setup and enabling a fully static binary build.
PRs: #3826, #3924 -
Proper JSON round-tripping
Fixed an issue causing custom claims to break if they were nested or unexpectedly typed. JSON round-trips are now correct.
PR: #3819 -
Speed up public key retrieval
Reduced overhead for the JWK public endpoint, solving CPU contention issues in large-scale deployments.
PRs: #3787, #3870 -
Fix Docker Compose references
The CLI now properly referencesdocker composeinstead ofdocker-compose, ensuring compatibility with modern Docker setups.
PR: #3815 -
Dependency upgrades
Bumpedfosite,ory/x,pgx/v5, and various third-party libraries for improved stability and performance. -
Updated docs
Updated examples, improved JWK documentation, added notes on Docker Compose usage, and refined OpenID Connect discovery docs. -
More tracing context
Tracing calls have been consistently standardized withotelx.End(), and additional context ensures better observability. -
Code generation & housekeeping
Various housekeeping tasks: pinned GHA versions, fixed minor comment typos, updated newsletters/links, and more.
To upgrade to 2.3.0, follow the usual steps:
- Back up your database (always recommended).
- Update your Hydra version in your Docker configuration, binary, or build to
v2.3.0. - Run
hydra migrate sql up(if using the new commands) or your usual migration procedure. - Restart your services and confirm that Hydra is up and running.
Check the migration docs for detailed information.
As always, we love hearing from our community. Here are some ways to get involved:
- Join our Slack: Ory Community Slack
- Ask questions on GitHub Discussions: Ory Hydra Discussions
- Submit bugs and feature requests: GitHub Issues
Thanks to all contributors for making Ory Hydra the best-in-class OAuth2 and OpenID Connect server.
For Ory Hydra v2.4.0 we are looking at another highly anticipated community-contributed feature, the OAuth 2.0 Device Authorization Grant!
Full Changelog: v2.2.0...v2.3.0
Happy building with Ory Hydra!
Breaking Changes
Going forward, OAuth2 Clients requesting an OpenID Connect flow must include the redirect_uri parameter or the request will be rejected.
Deleting consents no longer returns 404 in certain edge cases but instead always 204.
Bug Fixes
-
Advertise support for response_mode=form_post in OIDC discovery document (#3861) (9cc5f28)
-
Broken JSON round-tripping for custom claims (b36b701):
Adding custom claims with numerical types (think JavaScript Number) previously did not
round-trip through Hydra correctly. For example, passing UNIX timestamps in custom claims
would end up as floating points in exponential notation in the final token. That, in turn,
confused or broke downstream consumers of the token, including Kratos. -
Change comment on revokeOAuth2LoginSessions (#3853) (6d829dd)
-
Correct span names (554238b)
-
Correctly pass multiple token audiences and prompt parameters when performing the authorization code flow from the CLI (#3736) (632faef)
-
Cpu contention when reading JWKs and suppress generating duplicate JWKs (#3870) (d5f65c5):
Previously each concurrent caller would need to lock a shared mutex when reading or writing a given JWK set.
The read path now doesn't require locking a mutex at all and instead returns valid query results directly.The write path is now protected by a concurrency control mechanism (using x/sync/singleflight) to ensure only one JWK set is generated and persisted.
Note: Duplicate JWK sets may still be improperly generated if running more than one Hydra instance in a high traffic environment.
-
Do not iteratively delete records (#3766) (5ef20a2):
Resolves performance issues on some databases when deleting consent.
-
docs: Adjust note about SDK support on oauth2 flow endpoints (#3812) (d0e047c)
-
Error log when RP responds with status code 204 (#3731) (153e4b5)
-
Faster GetPublicKeys (#3787) (04c34aa):
GetPublicKeys used to fetch all keys in a set, even if they were actually not being used. This patch fixes that.
-
Improve docker set up (#3924) (8ca6cbd), closes #3914 #3683:
Improves the docker set up and removes some unused files.
-
Incorrect context passthru (fa50e3e)
-
Incorrect indices (#3778) ([cb0004b](https://github.com/ory/hydr...
Assets 48
v2.2.0
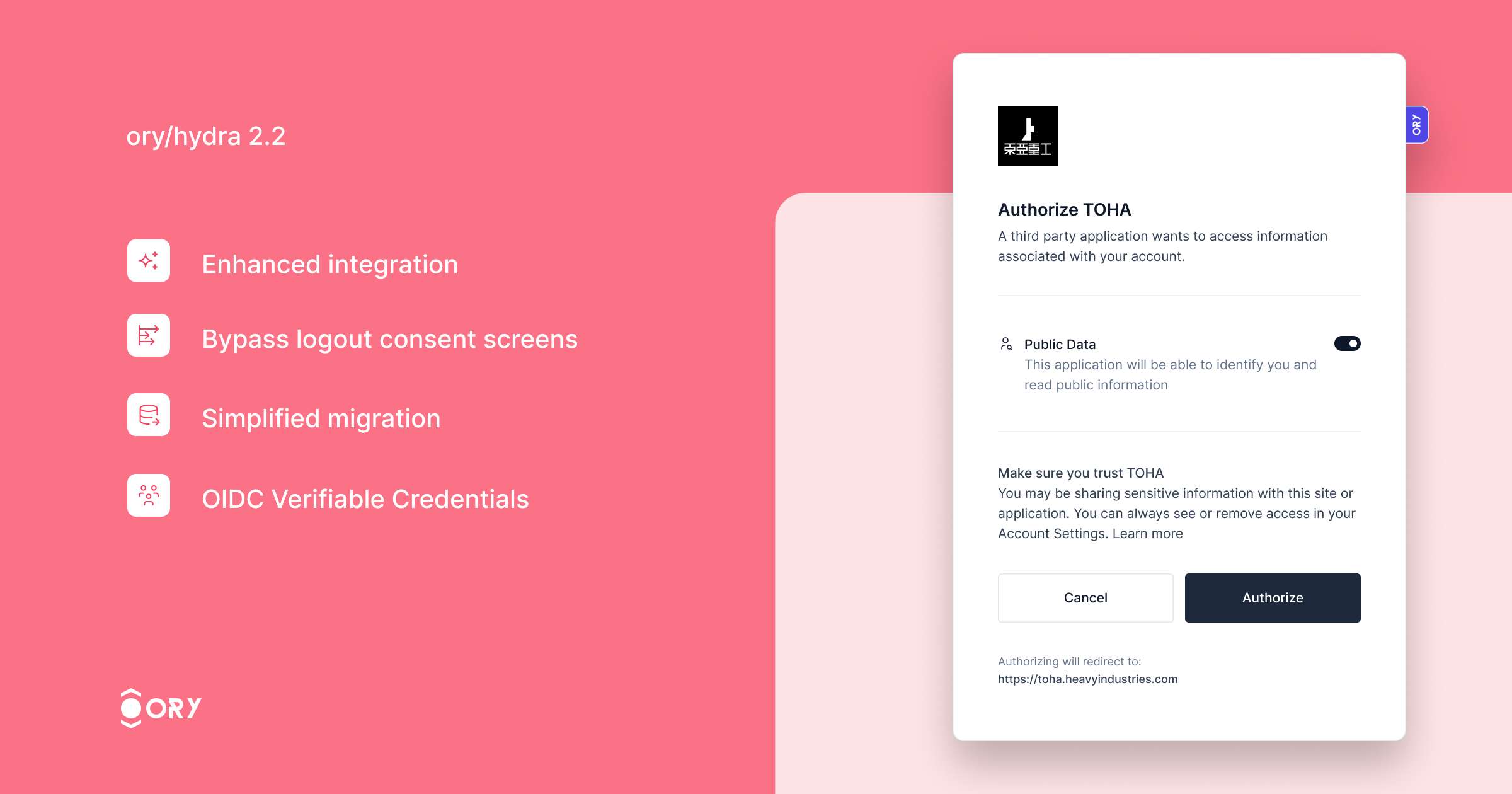
Ory Hydra, the OAuth2 and OpenID Connect server designed for web-scale deployments introduces over 6x higher OAuth2 throughput on a single PostgreSQL instance!
Want to check out Ory Hydra yourself? Try common OAuth2 flows in the Ory OAuth2 Get Started guide!
This version significantly enhances performance, processing over 6x more authorization flows than version 2.1, thanks to architectural improvements that minimize database interactions for login and consent processes.
Key improvements include:
- Enhanced integration with Ory Kratos, ensuring seamless synchronization of login and logout states across both services. Users logged out from Ory Hydra will automatically log out from Ory Kratos, enhancing security and user experience.
- The ability to bypass the logout consent screen for specific clients, streamlining the logout process.
- Simplified migration with the new feature to import OAuth2 Client IDs, making the transition to Ory Hydra smoother.
- Support for the OIDC Verifiable Credentials specification, expanding the server's capabilities in identity verification.
Thank all contributors who have made this release available!
Bug Fixes
-
Return empty slice if requested_scope or audience is null (#3711) (65165e7)
-
Correct id token type in token exchange response (#3625) (d1f9ba8):
Closes ory/client-go#2
-
Handle subject mismatch gracefully (#3619) (af0d477):
We now redirect to the original request URL if the subjects between
the remembered Hydra session and what was confirmed by the login
screen does not match. -
Handle token hook auth config (#3677) (1a40833):
- fix: handle token hook auth config
- fix: bump golangci-lint
-
Incorrect down migration (#3708) (8812e0e), closes /github.com/ory/hydra/pull/3705#discussion_r1471514014
-
Timeout in jwt-bearer grants when too many grants are available (#3692) (a748797)
-
Deflake ttl test (6741a49)
-
Only query access tokens by hashed signature (a21e945)
-
Reject invalid JWKS in client configuration / dependency cleanup and bump (#3603) (1d73d83)
-
Restore ability to override auth and token urls for exemplary app (#3590) (dfb129a)
-
Return proper error when the grant request cannot be parsed (#3558) (26f2d34)
Documentation
Features
-
Add prompt=registration (#3636) (19857d2):
Ory Hydra now supports a
registrationvalue for thepromptparameter of
the authorization request. When specifyingprompt=registration, Ory Hydra
will redirect the user to the URL found underurls.registration
(instead ofurls.login). -
Add skip_logout_consent option to clients (#3705) (2a653e6):
Adds a special field which disables the logout consent screen when performing OIDC logout.
-
Re-enable legacy client IDs (#3628) (5dd7d30):
This patch changes the primary key of the
hydra_clienttable. We do not expect issues, as that table is probably not overly huge in any deployment. We do however highly recommend to test the migration performance on a staging environment with a similar database setup. -
Remove flow cookie (#3639) (cde3a30):
This patch removes the flow cookie. All information is already tracked in the request query parameters as part of the {login|consent}_{challenge|verifier}.
-
Remove login session cookie during consent flow (#3667) (5f41949)
-
Add more resolution to events and collect client metrics (#3568) (466e66b)
-
Add state override (b8b9154)
-
Add support for OIDC VC (#3575) (219a7c0):
This adds initial support for issuing verifiable credentials
as specified in https://openid.net/specs/openid-connect-userinfo-vc-1_0.html.Because the spec is still in draft, public identifiers are
suffixed withdraft_00. -
Allow to disable claim mirroring ([#3563](https:...
Assets 48
v2.2.0-rc.3
Introduces logout compatibility with Ory Kratos.
Bug Fixes
- Add exceptions for internal IP addresses (#3608) (1f1121c)
- Add kid to verifiable credential header (#3606) (9f1c8d1)
- Deflake ttl test (6741a49)
- Docker build (#3609) (01ff9da)
- Enable CORS with hot-reloaded origins (#3601) (6f592fc)
- Only query access tokens by hashed signature (a21e945)
- Racy random string generation (#3555) (1b26c4c)
- Reject invalid JWKS in client configuration / dependency cleanup and bump (#3603) (1d73d83)
- Restore ability to override auth and token urls for exemplary app (#3590) (dfb129a)
- Return proper error when the grant request cannot be parsed (#3558) (26f2d34)
- Use correct tracer in middleware (#3567) (807cbd2)
Code Generation
- Pin v2.2.0-rc.3 release commit (ad8a4ba)
Features
-
Add more resolution to events and collect client metrics (#3568) (466e66b)
-
Add state override (b8b9154)
-
Add support for OIDC VC (#3575) (219a7c0):
This adds initial support for issuing verifiable credentials
as specified in https://openid.net/specs/openid-connect-userinfo-vc-1_0.html.Because the spec is still in draft, public identifiers are
suffixed withdraft_00. -
Allow to disable claim mirroring (#3563) (c72a316):
This PR introduces another config option called
oauth2:mirror_top_level_claimswhich may be used to disable the mirroring of custom claims into theextclaim of the jwt.
This new config option is an opt-in. If unused the behavior remains as-is to ensure backwards compatibility.Example:
oauth2: allowed_top_level_claims: - test_claim mirror_top_level_claims: false # -> this will prevent test_claim to be mirrored within ext
Closes #3348
-
Bump fosite and add some more tracing (0b56f53)
-
cmd: Add route that redirects to the auth code url (4db6416)
-
Propagate logout to identity provider (#3596) (c004fee):
- feat: propagate logout to identity provider
This commit improves the integration between Hydra and Kratos when logging
out the user.This adds a new configuration key for configuring a Kratos admin URL.
Additionally, Kratos can send a session ID when accepting a login request.
If a session ID was specified and a Kratos admin URL was configured,
Hydra will disable the corresponding Kratos session through the admin API
if a frontchannel or backchannel logout was triggered.- fix: add special case for MySQL
- chore: update sdk
- chore: consistent naming
- fix: cleanup persister
-
Support different jwt scope claim strategies (#3531) (45da11e)
Changelog
- 2c452ef autogen(docs): regenerate and update changelog
- 551c359 autogen(docs): regenerate and update changelog
- 93ebaee autogen(docs): regenerate and update changelog
- 7cfba84 autogen(docs): regenerate and update changelog
- cb64770 autogen(docs): regenerate and update changelog
- 938d4bb autogen(docs): regenerate and update changelog
- 0072ddf autogen(docs): regenerate and update changelog
- c30de7f autogen(docs): regenerate and update changelog
- 6c298b2 autogen(docs): regenerate and update changelog
- a547a74 autogen(docs): regenerate and update changelog
- 5704640 autogen(docs): regenerate and update changelog
- e586cc2 autogen(docs): regenerate and update changelog
- 2bdad2c autogen(docs): regenerate and update changelog
- dc878b8 autogen(docs): regenerate and update changelog
- 425c977 autogen(docs): regenerate and update changelog
- 339bf40 autogen(docs): regenerate and update changelog
- ea40d44 autogen(docs): regenerate and update changelog
- 71d1853 autogen(docs): regenerate and update changelog
- be85c29 autogen(docs): regenerate and update changelog
- 598c21d autogen(docs): regenerate and update changelog
- 42a9615 autogen(docs): regenerate and update changelog
- 330530d autogen(openapi): regenerate swagger spec and internal client
- 254a21b autogen(openapi): regenerate swagger spec and internal client
- ad8a4ba autogen: pin v2.2.0-rc.3 release commit
- 6631c21 autogen: render config schema
- 59ec76b chore(deps): bump semver from 5.7.0 to 5.7.2 (#3569)
- 9fd59e2 chore(deps): bump semver from 5.7.0 to 5.7.2 in /test/e2e/oauth2-client (#3570)
- 3c5c126 chore(deps): bump tough-cookie, @cypress/request and wait-on (#3592)
- 48d5df4 chore: add hperl as codeowner (#3607)
- efd9ca7 chore: bump deps (#3560)
- d5099cb chore: remove fosite branch override (#3599)
- 3914585 chore: replace fosite rewrite (#3564)
- 8ed2a2d chore: support in README (#3565)
- 1a1f504 chore: update repository templates to ory/meta@ac80097
- eb89af7 chore: update repository templates to ory/meta@af28aff
- 4db6416 feat(cmd): add route that redirects to the auth code url
- 749eb8d feat: add
hydra migrate statussubcommand (#3579) - 466e66b feat: add more resolution to events and collect client metrics (#3568)
- b8b9154 feat: add state override
- 219a7c0 feat: add support for OIDC VC (#3575)
- 8eed306 feat: allow Go migrations (#3602)
- 8900cbb feat: allow additional SQL migrations (#3587)
- c72a316 feat: allow to disable claim mirroring (#3563)
- 0b56f53 feat: bump fosite and add some more tracing
- 5bd9002 feat: parallel generation of JSON web key set (#3561)
- c004fee feat: propagate logout to identity provider (#3596)
- 45da11e feat: support different jwt scope claim strategies (#3531)
- 1f1121c fix: add exceptions for internal IP addresses (#3608)
- 9f1c8d1 fix: add kid to verifiable credential header (#3606)
- 6741a49 fix: deflake ttl test
- 01ff9da fix: docker build (#3609)
- 6f592fc fix: enable CORS with hot-reloaded origins (#3601)
- a21e945 fix: only query access tokens by hashed signature
- 1b26c4c fix: racy random string generation (#3555)
- 1d73d83 fix: reject invalid JWKS in client configuration / dependency cleanup and bump (#3603)
- dfb129a fix: restore ability to override auth and token urls for exemplary app (#3590)
- 26f2d34 fix: return proper error when the grant request cannot be parsed (#3558)
- 807cbd2 fix: use correct tracer in middleware (#3567)
Artifacts can be verified with cosign using this public key.
Assets 48
v2.2.0-rc.2
This release optimizes the performance of authorization code grant flows by minimizing the number of database queries. We acheive this by storing the flow in an AEAD-encoded cookie and AEAD-encoded request parameters for the authentication and consent screens.
BREAKING CHANGE:
- The client that is used as part of the authorization grant flow is stored in the AEAD-encoding. Therefore, running flows will not observe updates to the client after they were started.
- Because the login and consent challenge values now include the AEAD-encoded flow, their size increased to around 1kB for a flow without any metadata (and increases linearly with the amount of metadata). Please adjust your ingress / gateway accordingly.
Bug Fixes
- Version clash in apk install (24ebdd3)
Code Generation
- Pin v2.2.0-rc.2 release commit (b183040)
Features
Changelog
- 4194d75 autogen(docs): regenerate and update changelog
- 898aa00 autogen(docs): regenerate and update changelog
- b183040 autogen: pin v2.2.0-rc.2 release commit
- a8ecf80 feat: hot-reload Oauth2 CORS settings (#3537)
- 3ec683d feat: sqa metrics v2 (#3533)
- 24ebdd3 fix: version clash in apk install
Artifacts can be verified with cosign using this public key.
Assets 40
v2.1.2
We are excited to announce the next Ory Hydra release! This release includes the following important changes:
- Fixed a memory leak in the OpenTelemetry implementation, improving overall memory usage and stability.
- Added a missing index for faster janitor cleanup, resulting in quicker and more efficient cleanup operations.
- Fixed a bug related to SameSite in dev mode, ensuring proper functionality and consistency in handling SameSite attributes during development.
We appreciate your continuous support and feedback. Please feel free to reach out to us with any further suggestions or issues.
Bug Fixes
-
Add index on requested_at for refresh tokens and use it in janitor (#3516) (5b8e712)
-
Do not use prepared SQL statements and bump deps (#3506) (31b9e66)
-
sql: Incorrect JWK query (#3499) (13ce0d6):
persister_grant_jwkhad an OR statement without bracket leading to not using the last part of the query.
Code Generation
- Pin v2.1.2 release commit (d94ed6e)
Documentation
Features
Changelog
- 0e84c24 autogen(docs): generate and bump docs
- 9f37172 autogen(docs): regenerate and update changelog
- 872720b autogen(docs): regenerate and update changelog
- 4907223 autogen(docs): regenerate and update changelog
- ba45af0 autogen(docs): regenerate and update changelog
- 3703e5a autogen(docs): regenerate and update changelog
- ca85a17 autogen(docs): regenerate and update changelog
- 0e7e95f autogen(docs): regenerate and update changelog
- be8f726 autogen: add v2.1.1 to version.schema.json
- d94ed6e autogen: pin v2.1.2 release commit
- 20c6fa7 autogen: render config schema
- 400b9af chore(deps): bump @nestjs/core and @openapitools/openapi-generator-cli (#3493)
- f2f007d chore(deps): bump github.com/docker/distribution (#3514)
- b69a332 chore: bump ory/x (#3518)
- cf20054 chore: remove unneeded dependency (#3494)
- e2b7665 chore: update nodemon version for oauth2 client (#3503)
- b71a36b docs: incorrect json output format example (#3497)
- 083d518 feat: add --skip-consent flag to hydra cli (#3492)
- 13ce0d6 fix(sql): incorrect JWK query (#3499)
- 5b8e712 fix: add index on requested_at for refresh tokens and use it in janitor (#3516)
- eddf7f3 fix: disable health check request logs (#3496)
- 31b9e66 fix: do not use prepared SQL statements and bump deps (#3506)
- 5751fae fix: proper SameSite=None in dev mode (#3502)
- 1b1899e fix: sqa config values unified across projects (#3490)
Artifacts can be verified with cosign using this public key.
Assets 40
v2.1.1
We are excited to share this year's Q1 release of Ory Hydra: v2.1!
Highlights:
- Support for Datadog tracing (#3431).
- Ability to skip consent for trusted clients (#3451).
- Setting access token type in the OAuth2 Client is now possible (#3446).
- Revoke login sessions by SessionID (#3450).
- Session lifespan extended on session refresh (#3464).
- Token request hooks added for all grant types (#3427).
- Reduced SQL tracing noise (#3481).
Don't want to run the upgrade yourself? Switch to Ory Network!
Bug Fixes
- Double-hashed access token signatures (#3486) (8720b25), closes #3485
- Reduce SQL tracing noise (#3481) (6e1f545)
Code Generation
- Pin v2.1.1 release commit (6efae7c)
Changelog
- df16a26 autogen(docs): generate and bump docs
- ed2ac06 autogen(docs): regenerate and update changelog
- 6078f85 autogen(docs): regenerate and update changelog
- ddfbd65 autogen: add v2.1.0 to version.schema.json
- 6efae7c autogen: pin v2.1.1 release commit
- ad549d6 autogen: pin v2.1.1 release commit
- 2f7cda5 autogen: render config schema
- 0448284 chore: update ory/x (#3480)
- 8720b25 fix: double-hashed access token signatures (#3486)
- 6e1f545 fix: reduce SQL tracing noise (#3481)
Artifacts can be verified with cosign using this public key.
Assets 40
v2.1.0
We are excited to share this year's Q1 release of Ory Hydra: v2.1.0!
Highlights:
- Support for Datadog tracing (#3431).
- Ability to skip consent for trusted clients (#3451).
- Setting access token type in the OAuth2 Client is now possible (#3446).
- Revoke login sessions by SessionID (#3450).
- Session lifespan extended on session refresh (#3464).
- Token request hooks added for all grant types (#3427).
- Reduced SQL tracing noise (#3481).
Don't want to run the upgrade yourself? Switch to Ory Network!
Bug Fixes
Code Generation
- Pin v2.1.0 release commit (3649832)
Changelog
- 5c2e227 autogen(docs): regenerate and update changelog
- 3649832 autogen: pin v2.1.0 release commit
- 6e1f545 fix: reduce SQL tracing noise (#3481)
Artifacts can be verified with cosign using this public key.
Assets 40
v2.1.0-pre.2
autogen: pin v2.1.0-pre.2 release commit
Code Generation
- Pin v2.1.0-pre.2 release commit (3b1d87e)
Changelog
- 3b1d87e autogen: pin v2.1.0-pre.2 release commit
Artifacts can be verified with cosign using this public key.
Assets 40
v2.1.0-pre.1
autogen: pin v2.1.0-pre.1 release commit
Code Generation
- Pin v2.1.0-pre.1 release commit (2289e6b)
Changelog
- 2289e6b autogen: pin v2.1.0-pre.1 release commit
- 0d740d9 chore(deps): bump github.com/opencontainers/runc from 1.1.4 to 1.1.5 (#3476)
- c29b968 chore: update alpine version
Artifacts can be verified with cosign using this public key.