| CARVIEW |
Select Language
HTTP/2 200
date: Mon, 19 Jan 2026 19:41:06 GMT
content-type: text/html; charset=UTF-8
server: cloudflare
vary: Accept-Encoding
set-cookie: exp_csrf_token=deleted; expires=Thu, 01-Jan-1970 00:00:01 GMT; Max-Age=0; path=/; secure; HttpOnly; SameSite=Lax
set-cookie: exp_csrf_token=590eca9919c23cb1241350b9ed7474f32ccaf0b4; expires=Mon, 19-Jan-2026 21:41:05 GMT; Max-Age=7200; path=/; secure; HttpOnly; SameSite=Lax
set-cookie: PHPSESSID=t2ialgiv24kos96tq3eoeubfpb; path=/; secure; HttpOnly
cache-control: no-store, no-cache, must-revalidate
x-frame-options: SAMEORIGIN
x-frame-options: SAMEORIGIN
expires: Mon, 26 Jul 1997 05:00:00 GMT
last-modified: Mon, 19 Jan 2026 19:41:06 GMT
pragma: no-cache
x-xss-protection: 1; mode=block
x-content-type-options: nosniff
report-to: {"group":"cf-nel","max_age":604800,"endpoints":[{"url":"https://a.nel.cloudflare.com/report/v4?s=MDhEfCwKBqowmvfXdFfQ8b6XLqoyXXMDMia%2FMWAwuTKdcMczCYFZYEQItJXJFEE7%2BTgU7D4nl%2FBm%2FPFcrXPCDY5haNh9esgI212wzokzeze9BOtI"}]}
cf-cache-status: DYNAMIC
nel: {"report_to":"cf-nel","success_fraction":0.0,"max_age":604800}
content-encoding: gzip
cf-ray: 9c08cebb4de03b97-BOM
alt-svc: h3=":443"; ma=86400
Possible Security Vulnerability? | ExpressionEngine


avori
67 posts
2 months ago
 avori
avori
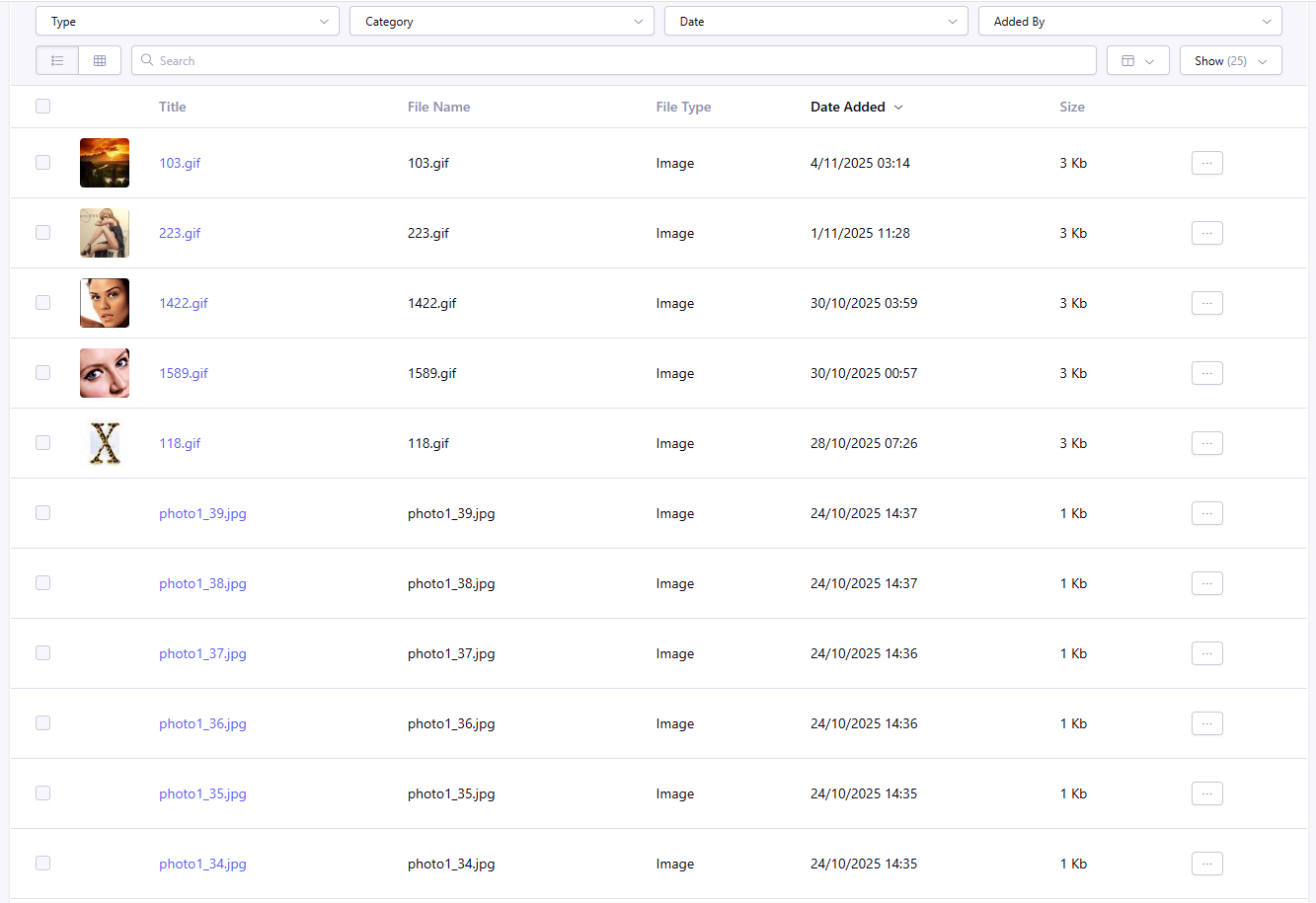
Hello All,
Recently found an email in my inbox from a gentleman named “Sahil”, saying he found a vulnerability with a website. I logged into the admin panel and found that a bunch of small few kb images have been added to the uploads.
I do have 2 front-end facing forms, one for candidates to apply for open positions, and a contact form. Both have a file upload. However no forms have been submitted with these images. I’m assuming someone, perhaps our guy “Sahil” was sending POST requests directly bypassing the form?
Anyway, how would I go about preventing this in the future?
Thanks, Viktor.

Tom Jaeger
449 posts
Reply
Privacy
Terms
Trademark Use
License
Packet Tide owns and develops ExpressionEngine. © Packet Tide, All Rights Reserved.


