| CARVIEW |
Model Context Guardrails for Your MCP
See every action. Control the context.
STAY SAFE
for security teams
Gateways are blind.
See every action.
Control the context.
See Platform Demo




AI agents can read files, execute tools, issue system commands, and access sensitive data through MCP servers and external integrations. Most organizations can’t see these actions — and can’t stop dangerous ones before they execute. BlueRock solves this with a security stack purpose-built for agentic workflows: safe MCP server selection, real-time action graphing, agent sandboxing, and pre-execution guardrails built into the runtime.
Secure Actions, Not Prompts
Prompt inspection and MCP gateways miss what agents actually do. They see requests — not the 47 tool calls, 12 database accesses, and 3 code execution steps agents take to accomplish them.
This is the shift from Agentic Protection 1.0 to 2.0:
1.0: Inspect prompts, filter at the edge, easily bypassed
2.0: See and secure actions at runtime, pre-execution enforcement
BlueRock is Agentic Protection 2.0


Three Execution Boundaries Every Agent Crosses
Every agentic operation — and every real incident — maps to one of three boundaries:


TOOLS
Agents call MCP tools and custom integrations.
Risk: Calling destructive tools, passing unsafe parameters, using shadow MCP servers.
DATA
Agents access, read, transform, and move data.
Risk: Reading sensitive data without context, exfiltrating data, crossing dev → prod boundaries.
EXECUTION
Agents execute code: shell commands, subprocesses, file operations.
Risk: Spawning shells in prod, executing unvalidated code, privilege escalation.
The BlueRock Agentic Protection Platform
One platform. Visibility first, control when you're ready.



MCP Trust Registry
Know which MCP servers are safe before you connect. Security ratings, tool exposure mapping, remediation guidance. The only security-focused MCP registry.
Explore the Registry



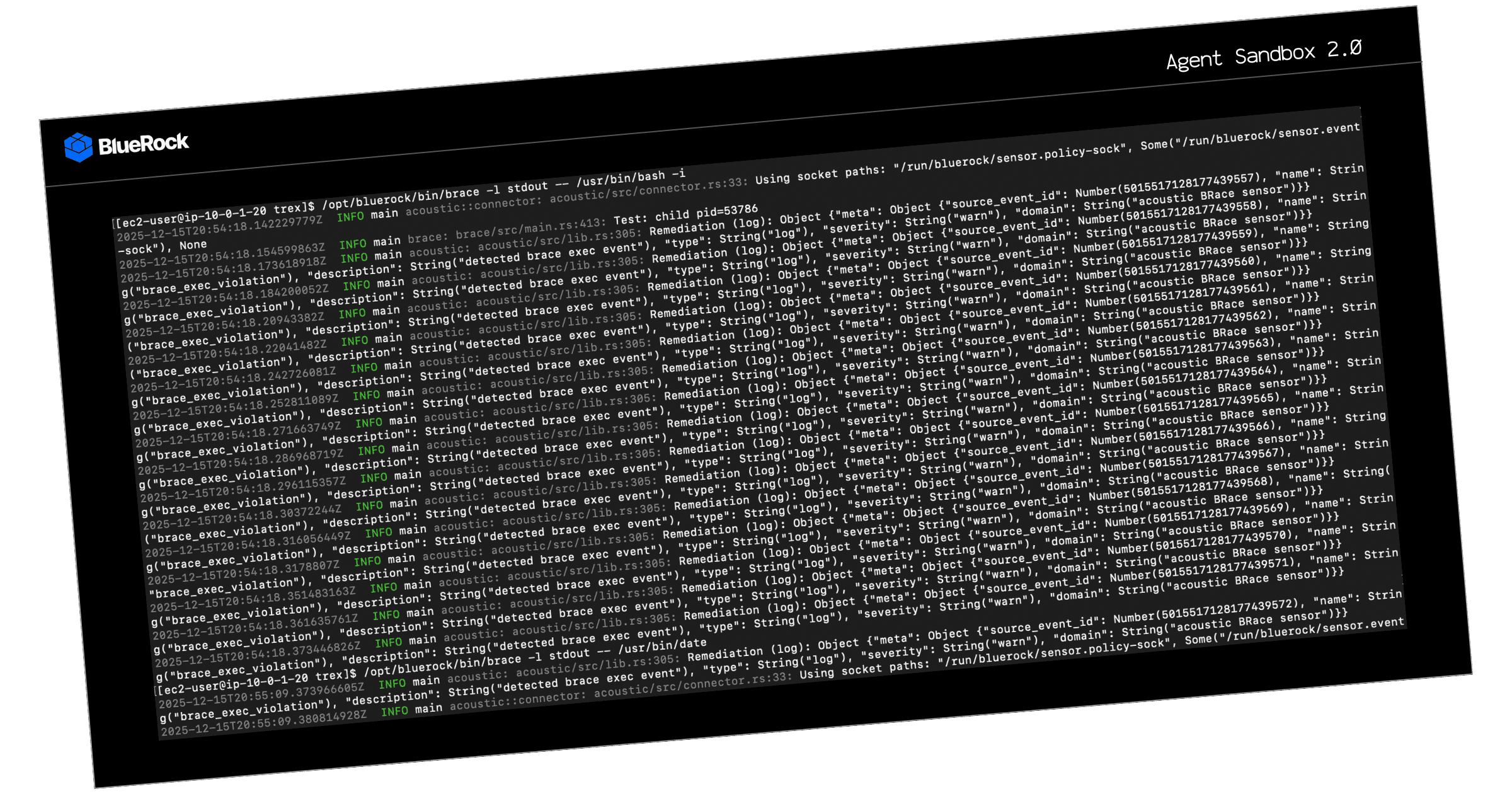
Agent Sandbox 2.0
Isolate, observe, and safely run agents in minutes. Zero-change or one-line CLI. Safe experimentation with full action visibility.
Request Sandbox 2.0 Access



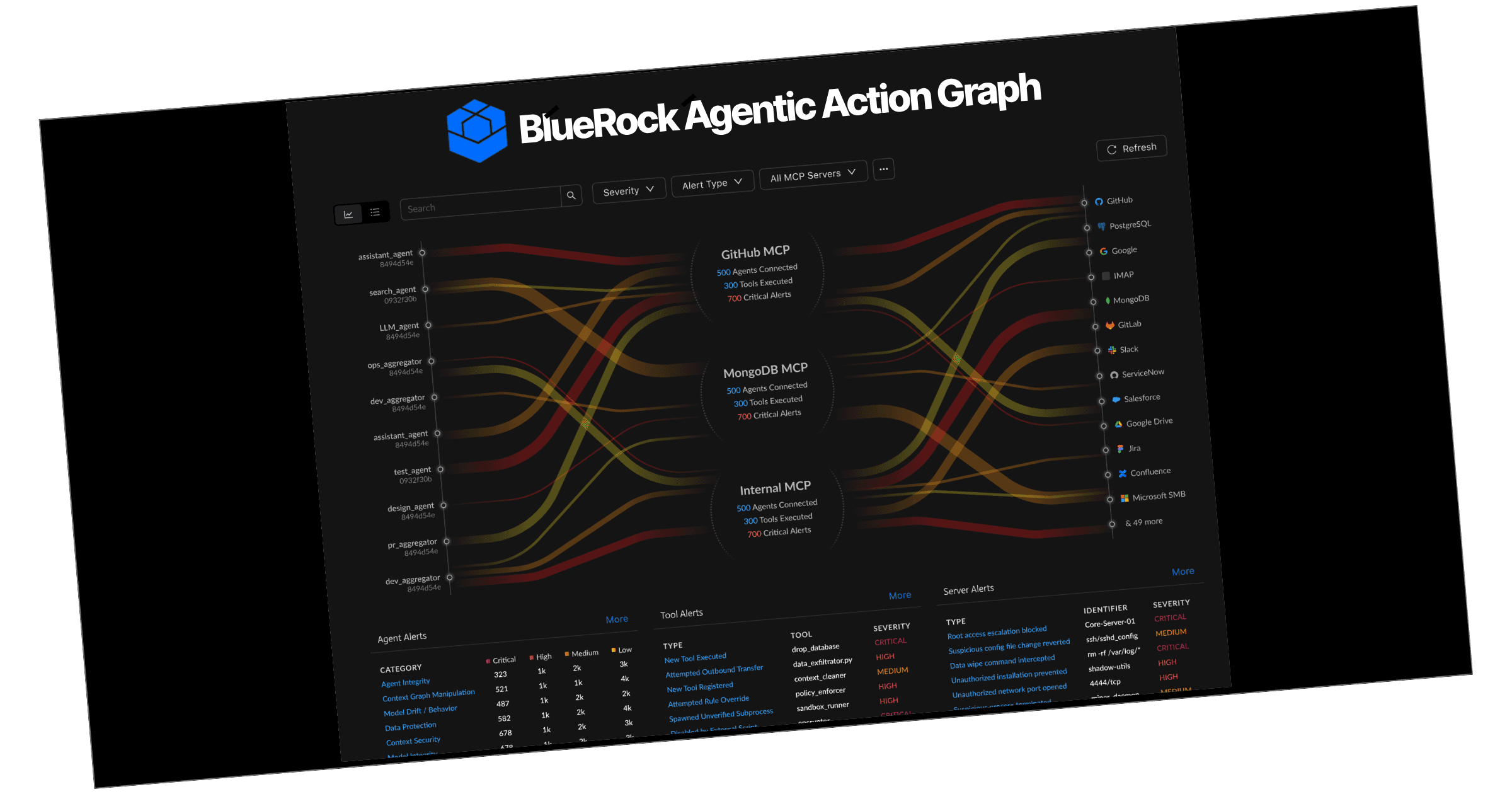
Agentic Visibility
See every agent action: tools → data → execution.
Unified action map, drift detection, MCP + agent telemetry correlation.
See the Agentic Action Map



MCP Server Protection
Block unsafe actions before they run (tools, data, execution). Tool governance, data access rules, execution guardrails. Pre-execution enforcement.
Learn How to Secure Actions
Choose safe MCP servers and tools before you connect.
The free MCP Server Registry scores servers, lists tools, and flags likely risks with remediation notes.
Scroll to see the full scan results.

Every agent path, every tool call, explained.
The BlueRock Agentic Visibility streams MCP + runtime events with policy outcomes. Search by agent, tool, resource, or path.


What you can do today
agent → tool
agent → tool
Agent
Agent
MCP Server
MCP Server
Trace invocations + parameters
Sandbox policies (allow/block; optional modify via scope/params)
Request visibility; drift drill-down
Trace invocations + parameters
Sandbox policies (allow/block; optional modify via scope/params)
Request visibility; drift drill-down
Inventory exposed tools; drift/versions
Invocation guardrails (approve/ allow-list + runtime controls)
Tool execution controls
Inventory exposed tools; drift/versions
Invocation guardrails (approve/ allow-list + runtime controls)
Tool execution controls
agent → data
agent → data
Agent
Agent
MCP Server
MCP Server
Observe read/write patterns; scope
Enforce egress limits; scope access
Deny-by-default resource access
Observe read/write patterns; scope
Enforce egress limits; scope access
Deny-by-default resource access
Monitor access patterns and transfers
Prevent mass exfiltration; stop token smuggling
MCP→agent key leakage controls
Monitor access patterns and transfers
Prevent mass exfiltration; stop token smuggling
MCP→agent key leakage controls
agent → code execution
agent → code execution
Agent
Agent
MCP Server
MCP Server
Observe process/file activity
Block unsafe execution; isolate artifacts
Runtime protections baked-in
Observe process/file activity
Block unsafe execution; isolate artifacts
Runtime protections baked-in
Observe server runtime & container drift
Harden: cmd injection, RCE, SSRF, path traversal, privilege escalation
Auditable blocks + artifact isolation
Observe server runtime & container drift
Harden: cmd injection, RCE, SSRF, path traversal, privilege escalation
Auditable blocks + artifact isolation
Deployment Options
Fast Mode (DevOps)
Launch BlueRock via a container or machine image.
In three minutes or less, agentic protection is running in an environment for developers to build their agentic workflows. Every instance/node running is default protected by BlueRock.
Flex Mode (Builders)
Build your agent or MCP server.
Launch Sandbox 2.0 via a single command-line and your agent is running inside or have an agent framework launch the sandbox. Launch your MCP server and get tool visibility and control. Devops can easily integrate the sandbox and/or MCP server into their CI/CD.
Compatibility
Agentic platforms: CrewAI, LangChain, Google ADK and many more
MCP servers: Python (now), Java (now), Node.js / TypeScript (Q1)
Infrastructure: AWS, Azure (Q1), GCP (Q1)
BlueRock Pre-Packaged Images: Amazon Linux 2023 v6.12, Ubuntu v24.x, Amazon Bottlerocket v1.43
Observability: Any OTEL-native event collector
IaC: Terraform, CloudFormation
Answers to common questions about BlueRock and agentic security
BlueRock helps teams see every agentic action across agents, tools, data, and runtime—and enforce guardrails before risky actions execute.
These FAQs cover what you get, how it works, and how to get started.
What is the BlueRock Agentic Protection Platform?
BlueRock is the first security platform purpose-built to see and secure autonomous agent actions across tools, data, and execution before they run. Unlike gateways that inspect prompts at the edge, BlueRock operates at runtime—where agents actually execute—to provide visibility, control, and pre-execution enforcement.
How is BlueRock different from MCP gateways?
What signals does BlueRock capture?
What products are included in the platform?
How do we get started with BlueRock?
Answers to common questions about BlueRock and agentic security
BlueRock helps teams see every agentic action across agents, tools, data, and runtime—and enforce guardrails before risky actions execute.
These FAQs cover what you get, how it works, and how to get started.
What is the BlueRock Agentic Protection Platform?
BlueRock is the first security platform purpose-built to see and secure autonomous agent actions across tools, data, and execution before they run. Unlike gateways that inspect prompts at the edge, BlueRock operates at runtime—where agents actually execute—to provide visibility, control, and pre-execution enforcement.
How is BlueRock different from MCP gateways?
What signals does BlueRock capture?
What products are included in the platform?
How do we get started with BlueRock?
Answers to common questions about BlueRock and agentic security
BlueRock helps teams see every agentic action across agents, tools, data, and runtime—and enforce guardrails before risky actions execute.
These FAQs cover what you get, how it works, and how to get started.
What is the BlueRock Agentic Protection Platform?
BlueRock is the first security platform purpose-built to see and secure autonomous agent actions across tools, data, and execution before they run. Unlike gateways that inspect prompts at the edge, BlueRock operates at runtime—where agents actually execute—to provide visibility, control, and pre-execution enforcement.
How is BlueRock different from MCP gateways?
What signals does BlueRock capture?
What products are included in the platform?
How do we get started with BlueRock?

Control the context. Trust the outcome.
Works with the frameworks you already use.
See and secure autonomous agent actions across tools, data, and execution before they run — at runtime.

Control the context. Trust the outcome.
Works with the frameworks you already use.
See and secure autonomous agent actions across tools, data, and execution before they run — at runtime.

Control the context. Trust the outcome.
Works with the frameworks you already use.
See and secure autonomous agent actions across tools, data, and execution before they run — at runtime.

