| CARVIEW |
Stop babysitting security data, start putting it to work
Axoflow, the Security Data Layer is the foundation for your SIEM and analytics tools enabling the use of AI, up to 70% faster investigations, and more than 50% reduction in SIEM spend by feeding them with actionable data.
From the creators of syslog-ng.

Our Technologies are Trusted by:

“Most security platforms claim to be built for the AI era. Very few actually are. What impressed me about Axoflow was how seamlessly it automates the messy, thankless work of preparing data—turning noisy, fragmented streams into something AI can actually reason over. Running an MSSP, I see this data preparation challenge across dozens of client environments daily. I know how much time, budget, and talent that usually takes. Axoflow gets it done in minutes, not months.”

“Security teams are drowning in data and starving for insight. As we move toward more automated, AI-driven workflows, the ability to reliably collect, normalize, and act on security data in real time isn’t just a nice-to-have—it’s foundational. Any progress in this space that reduces noise and improves signal fidelity is a big win for modern security operations.”

“There’s no shortage of teams chasing to solve the security data problem. What stood out about Axoflow was their discipline. Instead of overpromising, they built something that actually works — fast to value, lean in architecture, and built to massive scale. That kind of clarity is rare in startups.”

“We’ve delivered countless log management deployments across APAC built on syslog-ng, so when we first saw Axoflow, it immediately felt familiar—but sharper. Having worked closely with Balázs Scheidler for over a decade, we knew anything he put his name behind would be worth serious consideration. What stood out this time was just how much complexity Axoflow removes. It distills decades of operational experience into a solution purpose-built for today’s security teams.”

“Axoflow’s strengths lie in its automation depth and operational flexibility… its classification-driven engine is a differentiator which handles reduction, normalization, and routing without regex or manual tuning… integration health is another strong point, with detailed metrics on drops, delays, queues, and host resources.”
The Only Security Data Layer That Ends Pipeline Maintenance
At Axoflow, we don’t pretend regex doesn’t exist. We just make sure you never have to deal with it.
We’ve built the only Security Data Layer that takes full ownership of the regex, the parsers, and the endless maintenance of security data every other pipeline pushes onto you.
Axoflow continuously classifies, normalizes, and manages your data - automatically. All behind the scenes.
Your team doesn’t maintain pipelines. Your team runs security.
This isn’t another pipeline. It’s freedom from pipeline work - and the foundation of the Autonomous Security Data Layer that finally lets you focus on what matters: using your data to protect your enterprise.
- When formats change, we adapt
- When things drift, we fix it
- When new data appears, we handle it
- No approvals
- No grok tuning
- No “schema drift” tickets

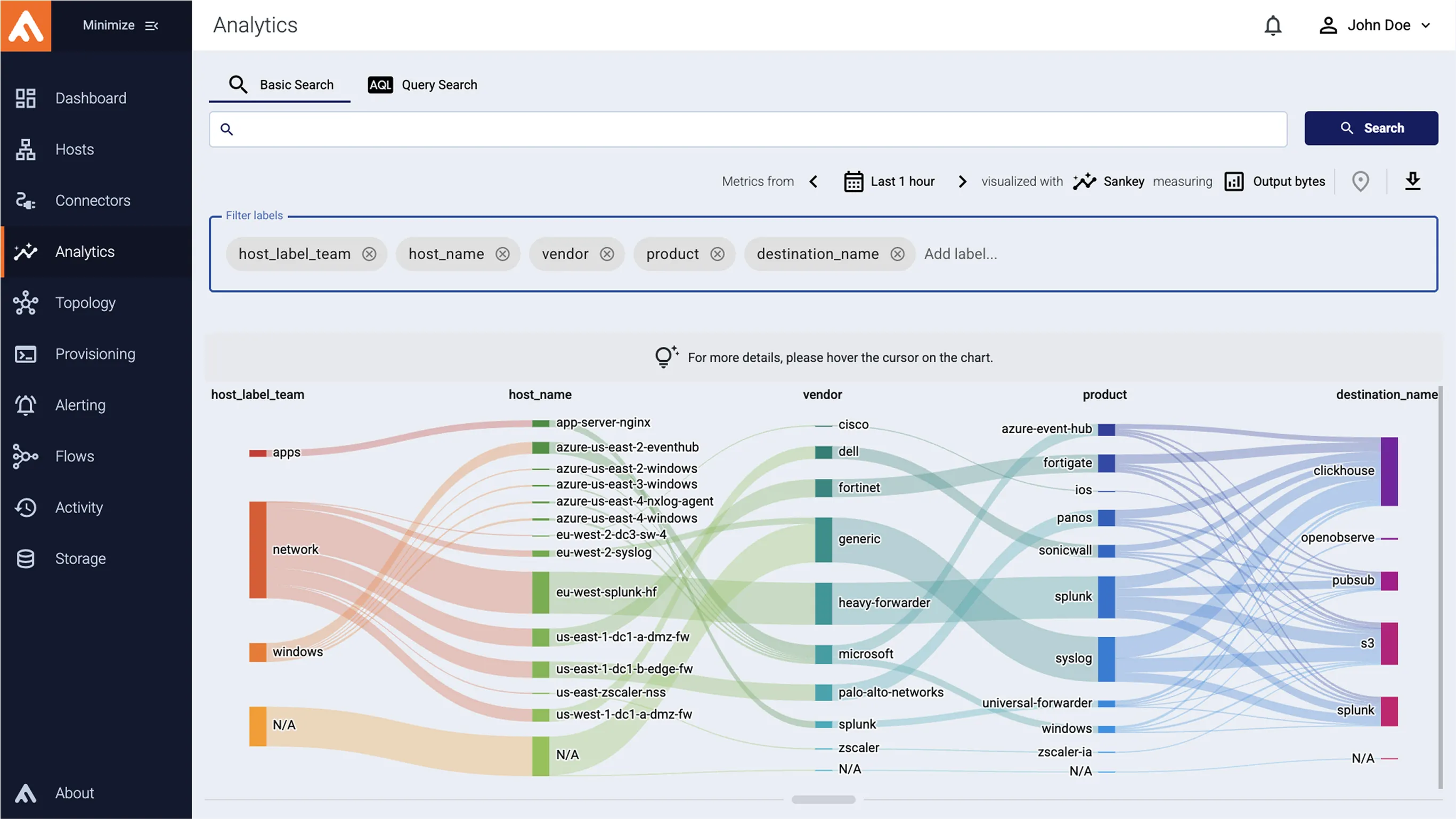
How automated security data curation works?
Collection
Collect security data from any source
Syslog
Windows
Cloud services
Applications
Kubernetes
Real-time data IQ
This is where the magic happens
Built on 25+ Years of Pipeline Mastery, Not AI Theater
When your data hits AxoRouter, it’s automatically classified using a decision tree engineered and continuously refined by our veteran cybersecurity team—augmented with supervised AI.
This isn’t some brittle regexp or hand-wavy “AI theater.” It’s a purpose-built engine that actually understands:
- What data is flowing through
- Which pieces carry security relevance
Our automations then use these labels to decide what pre-processing steps need to be applied automatically and where the data should be routed.
Automatic Pre-Processing
Reduce, Transform, Pre-Process Automatically
Parse
Accurately identify and format log fields—no regex or manual mapping needed.
Pre-process
Normalize field names, fix timestamp or other inconsistencies or use your custom rules to clean your data before ingestion.
Reduce
Drop, deduplicate, and trim redundant events to cut ingestion costs without losing detection fidelity.
Normalize
Translate logs to a unified schema, aligned with your SIEM or data lake, so detection rules just work.
Anonymize
Remove or obfuscate sensitive data inline to maintain privacy and reduce compliance risk.
Enrich
Geo-IP, asset metadata, or threat intel—all added inline to boost investigation speed.
Route
Tag and forward data by type, policy or however you need it—then use Axoflow’s policy-based routing to handle the rest.
Extend
Unleash limitless flexibility by dropping in your own code, scripts, or logic at any stage.
Ingestion
Then Route It To The Respective Destinations
SIEM
Observabilty
Data Lake
Archive
Message Queues
Axoflow Storage
Axoflow is the Security Data Layer - Pipeline, Storage, and AI that work as one
Axoflow does the whole data journey: collect + pre-process (Pipeline), keep & query (Storage), and apply intelligence (AI) - as a single, integrated layer.
Classification, parsing, normalization, reduction, label-based routing, temporal buffering, federated search across Axoflow storage solutions, replay, and policy tiering - all included and designed to work together.
You focus on detections and investigations. We handle the details.
Everything works together
Details handled, end-to-end
Store smart, search anywhere
investigations
Industry Insights
“If you’re not using data pipeline management for security and IT, you need to.”
“By 2026, 40% of log telemetry will be processed through a telemetry pipeline product, an increase from less than 10% in 2022.”
Axoflow Platform
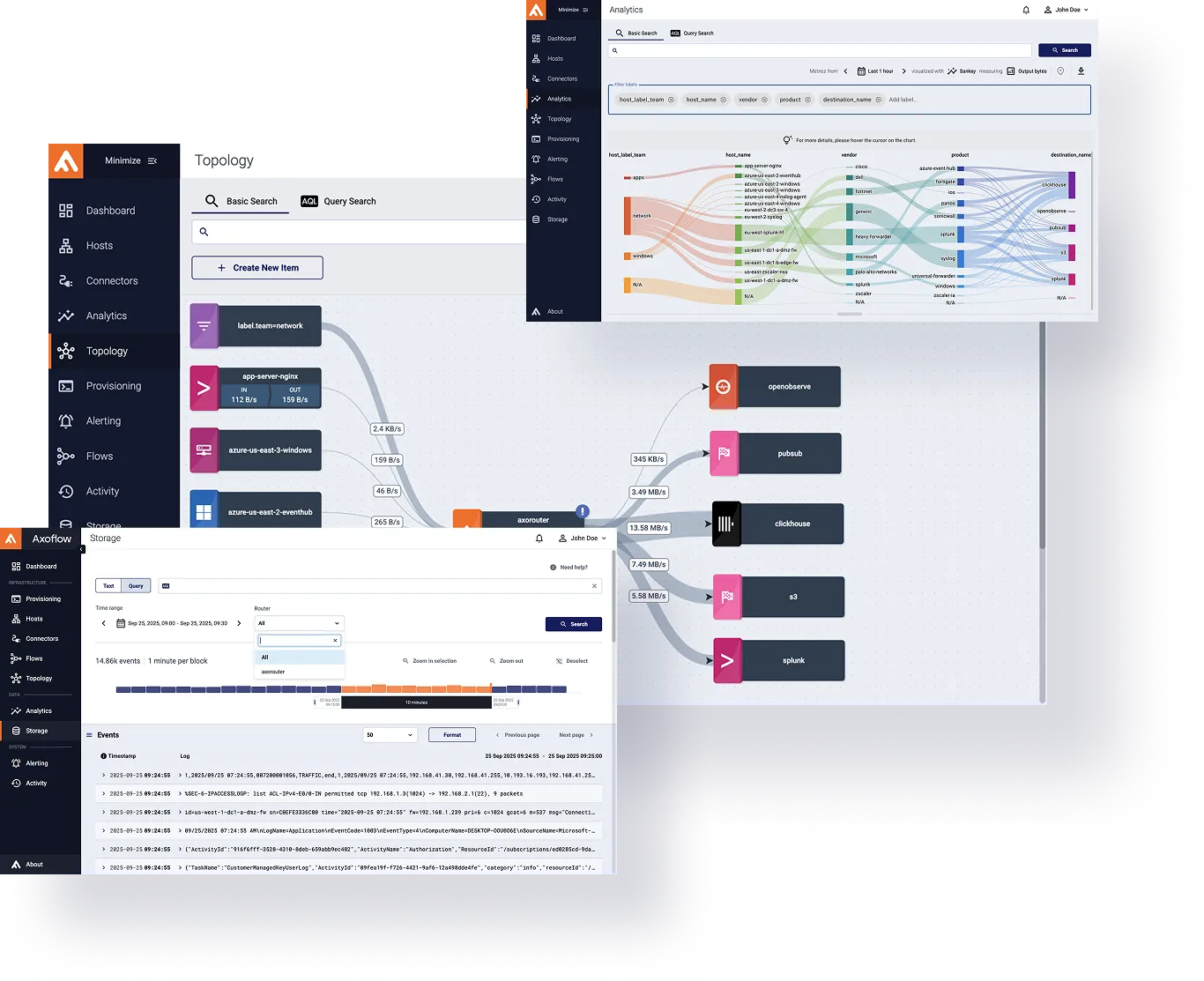
Automatic Data Curation in the Pipeline
- Curation happens before it reaches the destination reducing data ingestion costs
- The pipeline automatically identifies and classifies where the data was coming from
- Enriches it with relevant context like geolocation if needed
- Finally, converts it to a destination-optimized format
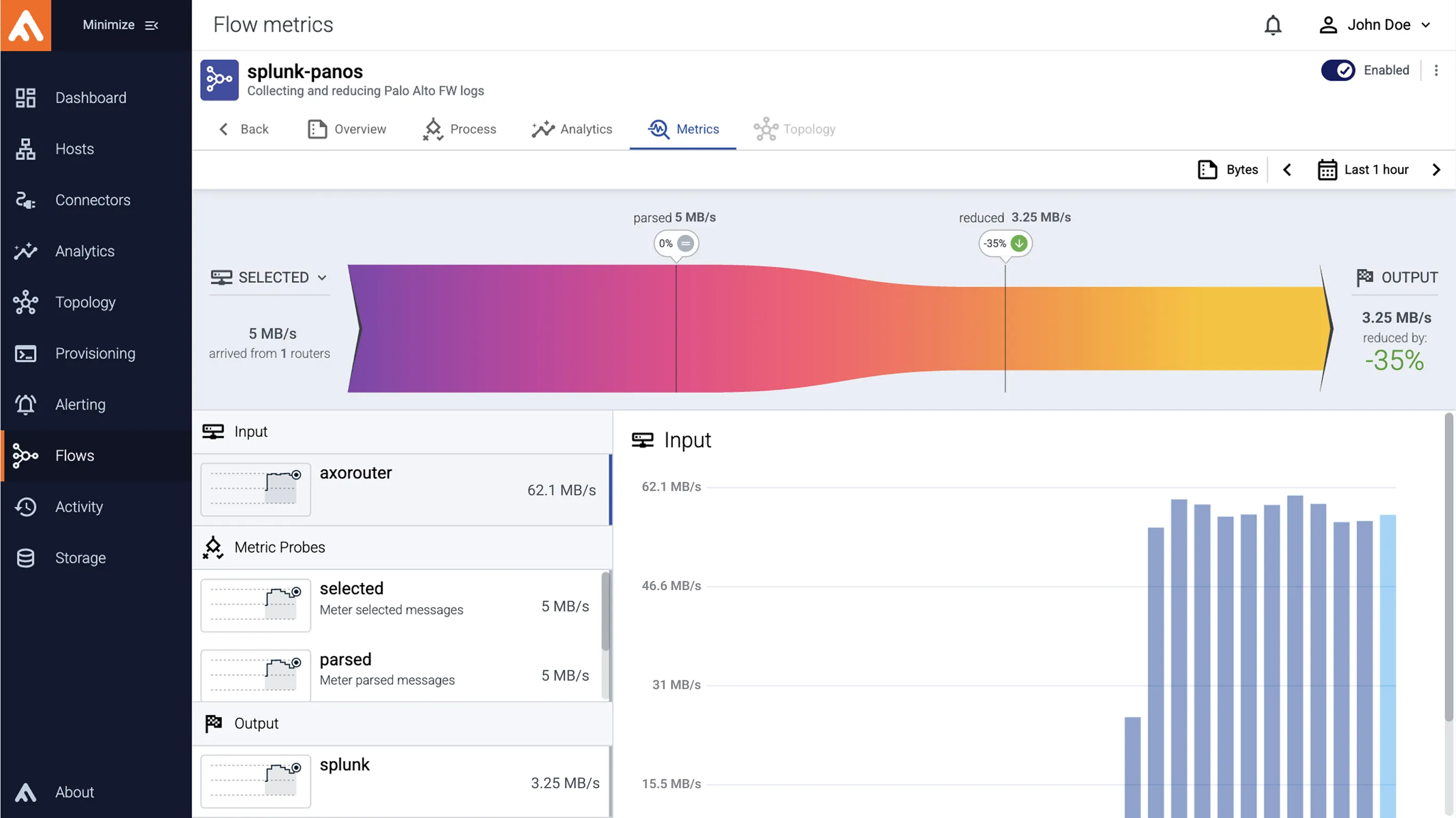
Efficient Pipeline Management
- Remove infrastructure redundancy and consolidate data volume
- Manage data collection with zero-maintenance connectors
- Increase data reliability with a dramatic drop in data losses, along with full visibility into pipelines
- Optimize traffic via distributed collection and single-pane-of-glass management
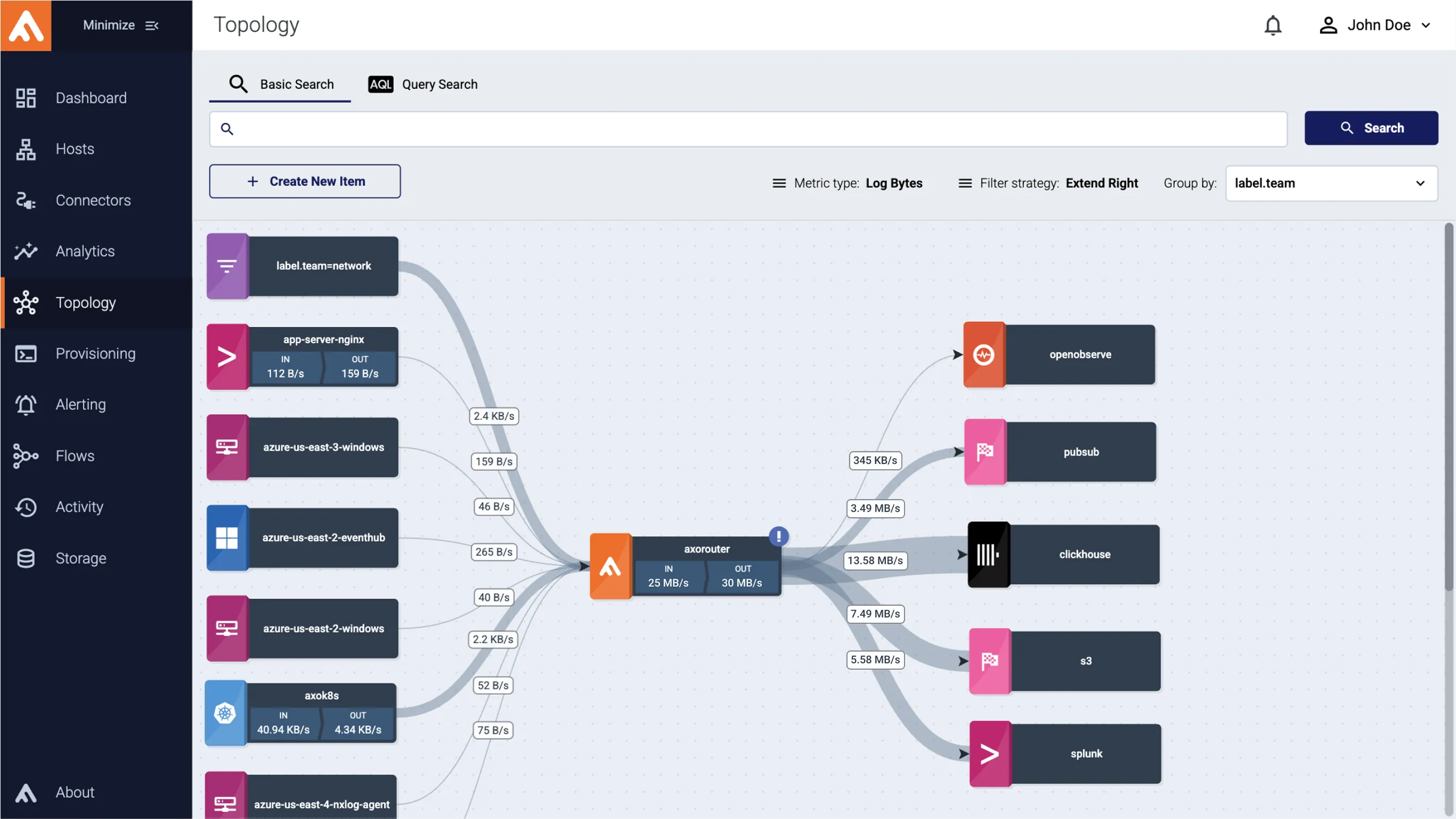
Security Data Pipelines Support GRC
- Know what you collect and why
- Organize data flows and retention based on your policies
- Avoid compliance breaches by gaining observability over your data transport
- Automatically route non-critical or unclaimed data to low-cost storage
Why Axoflow?
Automated Data Curation
High Quality, Reduced Security Data
Unparalleled Simplicity And Visibility
Proven Technology At Petabyte Scale
Platform-Agnostic Fleet Management
Experts In On-Prem And Cloud-Native Security Data
Check out our latest news


Axoflow Scores Double Win at Top InfoSec Innovator Awards


Comprehensive Storage Solutions for the Security Data Layer


How Data Pipelines Supercharge AI in Cyber Defense at GovWare 2025

Have a question?
We’re here to help you tackle the problem of low quality data that comes in ever-increasing volumes. If you’d like to solve this challenge more reliably, with drastically less effort, and cost, don’t hesitate to reach out.





















