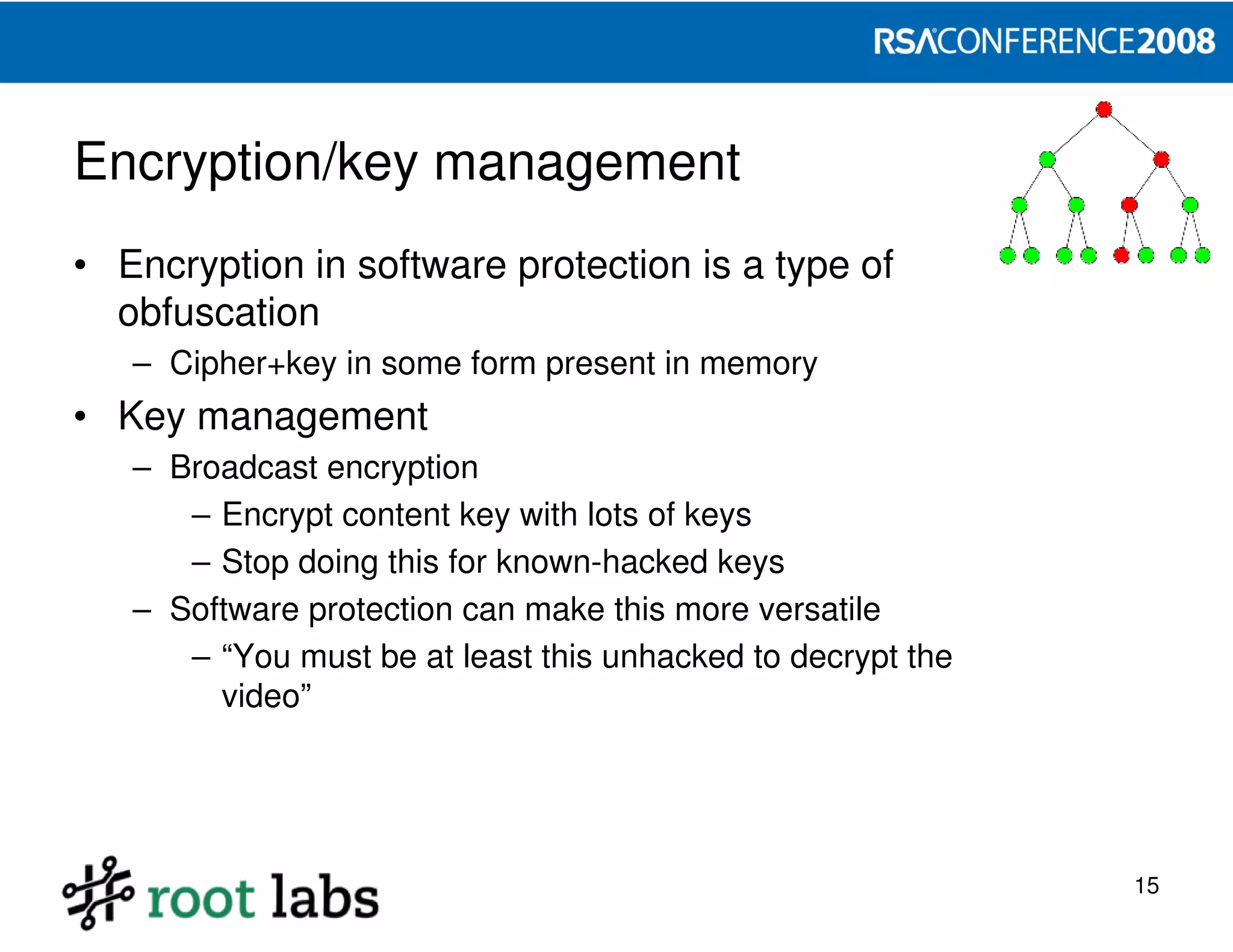
HTTP/2 301
server: envoy
x-frame-options: SAMEORIGIN
cache-control: public, s-maxage=86400, max-age=0, must-revalidate
location: https://www.slideshare.net/slideshow/designing-and-attacking-drm-rsa-2008/1563021
x-envoy-upstream-service-time: 279
p3p: CP="OTI DSP COR CUR ADM DEV PSD IVD CONo OUR IND"
x-content-type-options: nosniff
accept-ranges: bytes
age: 0
date: Sat, 11 Oct 2025 16:24:00 GMT
via: 1.1 varnish
x-served-by: cache-bom-vanm7210035-BOM
x-cache: MISS
x-cache-hits: 0
x-timer: S1760199840.422998,VS0,VE526
vary: accept-encoding, x-bot
set-cookie: browser_id=c66a3b09-a39e-450a-94c9-f65203b9002b; Domain=.slideshare.net; Path=/; Expires=Thu, 10 Oct 2030 16:24:00 GMT
strict-transport-security: max-age=63072000; includeSubDomains; preload
alt-svc: h3=":443";ma=86400,h3-29=":443";ma=86400,h3-27=":443";ma=86400
content-length: 81
HTTP/2 200
content-type: text/html; charset=utf-8
server: envoy
x-frame-options: SAMEORIGIN
cache-control: public, s-maxage=86400, max-age=0, must-revalidate
x-powered-by: Next.js
etag: "15awqk23u8ynpp0"
content-encoding: gzip
x-envoy-upstream-service-time: 276
p3p: CP="OTI DSP COR CUR ADM DEV PSD IVD CONo OUR IND"
x-content-type-options: nosniff
accept-ranges: bytes
age: 1
date: Sat, 11 Oct 2025 16:24:03 GMT
via: 1.1 varnish
x-served-by: cache-bom-vanm7210035-BOM
x-cache: MISS
x-cache-hits: 0
x-timer: S1760199841.962488,VS0,VE2073
vary: accept-encoding, x-bot
strict-transport-security: max-age=63072000; includeSubDomains; preload
alt-svc: h3=":443";ma=86400,h3-29=":443";ma=86400,h3-27=":443";ma=86400
content-length: 135786
Designing and Attacking DRM (RSA 2008) | PDF
Recommended
PPTX
Root via sms. 4G security assessment
PDF
Root via SMS: 4G access level security assessment, Sergey Gordeychik, Alexand...
PPTX
BlueHat v17 || “_____ Is Not a Security Boundary." Things I Have Learned and...
PDF
Troopers15 Lightning talk: VMI & DRAKVUF
PDF
SD-WAN Internet Census, Zeronighst 2018
PDF
Malware Collection and Analysis via Hardware Virtualization
PPTX
Reverse Engineering the TomTom Runner pt. 1
PDF
Windows Systems & Code Signing Protection by Paul Rascagneres
PPTX
CheckPoint: Anatomy of an evolving bot
PDF
DEFCON 22: Bypass firewalls, application white lists, secure remote desktops ...
PPTX
BlueHat v17 || Raising the Bar: New Hardware Primitives for Exploit Mitigations
PDF
Defcon 22-zoltan-balazs-bypass-firewalls-application-whiteli
PDF
Cloud Security with LibVMI
PPTX
BlueHat v17 || Wannacrypt + Smbv1.0 Vulnerability = One of the Most Damaging ...
PPTX
How to drive a malware analyst crazy
PPTX
BlueHat v17 || Securing Windows Defender Application Guard
PDF
Automated Malware Analysis and Cyber Security Intelligence
PPTX
Virtual Machine Introspection - Future of the Cloud
PPTX
BSides London 2015 - Proprietary network protocols - risky business on the wire.
PPTX
Shameful Secrets of Proprietary Network Protocols - OWASP AppSec EU 2014
PPTX
BlueHat v17 || All Your Cloud Are Belong to Us; Hunting Compromise in Azure
PDF
PDF
Defcon 22-jesus-molina-learn-how-to-control-every-room
PPTX
Hacker Halted 2014 - Post-Exploitation After Having Remote Access
PDF
31c3 Presentation - Virtual Machine Introspection
PDF
50 Shades of Fuzzing by Peter Hlavaty & Marco Grassi
PDF
Top 10 secure boot mistakes
PDF
Cracking Into Embedded Devices - Hack in The Box Dubai 2008
PDF
Bypassing patchguard on Windows 8.1 and Windows 10
PDF
When is something overflowing
More Related Content
PPTX
Root via sms. 4G security assessment
PDF
Root via SMS: 4G access level security assessment, Sergey Gordeychik, Alexand...
PPTX
BlueHat v17 || “_____ Is Not a Security Boundary." Things I Have Learned and...
PDF
Troopers15 Lightning talk: VMI & DRAKVUF
PDF
SD-WAN Internet Census, Zeronighst 2018
PDF
Malware Collection and Analysis via Hardware Virtualization
PPTX
Reverse Engineering the TomTom Runner pt. 1
PDF
Windows Systems & Code Signing Protection by Paul Rascagneres
What's hot
PPTX
CheckPoint: Anatomy of an evolving bot
PDF
DEFCON 22: Bypass firewalls, application white lists, secure remote desktops ...
PPTX
BlueHat v17 || Raising the Bar: New Hardware Primitives for Exploit Mitigations
PDF
Defcon 22-zoltan-balazs-bypass-firewalls-application-whiteli
PDF
Cloud Security with LibVMI
PPTX
BlueHat v17 || Wannacrypt + Smbv1.0 Vulnerability = One of the Most Damaging ...
PPTX
How to drive a malware analyst crazy
PPTX
BlueHat v17 || Securing Windows Defender Application Guard
PDF
Automated Malware Analysis and Cyber Security Intelligence
PPTX
Virtual Machine Introspection - Future of the Cloud
PPTX
BSides London 2015 - Proprietary network protocols - risky business on the wire.
PPTX
Shameful Secrets of Proprietary Network Protocols - OWASP AppSec EU 2014
PPTX
BlueHat v17 || All Your Cloud Are Belong to Us; Hunting Compromise in Azure
PDF
PDF
Defcon 22-jesus-molina-learn-how-to-control-every-room
PPTX
Hacker Halted 2014 - Post-Exploitation After Having Remote Access
PDF
31c3 Presentation - Virtual Machine Introspection
PDF
50 Shades of Fuzzing by Peter Hlavaty & Marco Grassi
PDF
Top 10 secure boot mistakes
PDF
Cracking Into Embedded Devices - Hack in The Box Dubai 2008
Viewers also liked
PDF
Bypassing patchguard on Windows 8.1 and Windows 10
PDF
When is something overflowing
PDF
Foundations of Platform Security
PDF
Copy Protection Wars: Analyzing Retro and Modern Schemes (RSA 2007)
PDF
ACPI and FreeBSD (Part 2)
PDF
Crypto Strikes Back! (Google 2009)
PDF
When Crypto Attacks! (Yahoo 2009)
PDF
Using FreeBSD to Design a Secure Digital Cinema Server (Usenix 2004)
PDF
ACPI and FreeBSD (Part 1)
PDF
Highway to Hell: Hacking Toll Systems (Blackhat 2008)
PDF
Don't Tell Joanna the Virtualized Rootkit is Dead (Blackhat 2007)
PDF
PPTX
PPTX
PDF
TLS/SSL MAC security flaw
PDF
TLS/SSL Protocol Design 201006
PDF
DeathNote of Microsoft Windows Kernel
PDF
PPTX
Windows Kernel Exploitation : This Time Font hunt you down in 4 bytes
Similar to Designing and Attacking DRM (RSA 2008)
PPTX
Vulnerabilities of machine learning infrastructure
PPTX
Mark Minasi Introducing Windows 7
PPTX
PDF
Secure Programming With Static Analysis
PPTX
PDF
An Introduction To Android
PPTX
Windows optimization and customization
PPTX
Sandbox detection: �leak, abuse, test - Hacktivity 2015
PDF
PDF
Scaling Rails with memcached
PDF
Challenges In Managing Embedded Product Development
PDF
PDF
[CB20] Reverse Engineering archeology : Reverse engineering multiple devices ...
PDF
Static Analysis Techniques For Testing Application Security - Houston Tech Fest
PDF
PDF
Cryptography in PHP: Some Use Cases
PPTX
Adversarial Post Ex - Lessons from the Pros
PPTX
Adversarial Post-Ex: Lessons From The Pros
PDF
Just In Time Scalability Agile Methods To Support Massive Growth Presentation
PDF
Working With People Adl Uni
Recently uploaded
PDF
Session 2 - Specialized AI Associate Series: Orchestrator Deep-Dive and UiPa...
PDF
Cloud and internet-of-things secure integration along with security concerns
PDF
TrustArc Webinar - The Future of Third-Party Privacy Risk: Trends, Tactics & ...
PDF
Certificate of Completion For Getting Started With Azure
PDF
Bringing Ideas to Life: Visualization and Virtual Servers Explained with Powe...
PDF
Phishing for Answers: A Tech Filler Quiz.pdf
PDF
Redefining HR Content Creation: Job Description Automation with UiPath's Agen...
PDF
From Source Code to Source of Truth_ 30 Years of Open Source Database Evolution
PPTX
Lightning_talk_Mojo comparision of python vs mojo performance
PDF
The Role of Human Experiences (HX) in GenAI Adoption
PDF
Certified Kubernetes Security Specialist (CKS): Unit 5
PPTX
DOC-20250918-WA0002.pptx Understanding the World Around Us
PPTX
UiPath Platform: Architecture & Context [1/3]
PDF
How to get started with Agentic Automation
PPTX
hackathon[1][1].pptx Cost-Effective Detection of LV Line Breakage
PPTX
"Don’t clone infrastructure — isolate data: ephemeral PR environments in a sh...
PDF
Writing GPU-Ready AI Models in Pure Java with Babylon
PDF
Dr. PANKAJ DHUSSA The near side of the Moon By NASA's Lunar Reconnaissance Or...
PDF
Neural Networks in a Nutshell: A practical review and usage
PDF
Starting a Customer Education Program: Taking Your Training to Them