| CARVIEW |

- Home
-
Topics

-
Blogs

-
News

-
Community

-
Industry

Blogs
Breaking Ground: Historic Launch of UN Global Mechanism for Cyberspace Governance
 The international community has long struggled with the challenge of translating international law into actionable norms and practices in cyberspace. The conclusion of the United Nations Open-Ended Working Group (OEWG) on the security of and in the use of information and communications technologies 2021-2025 marks a vital milestone in that ongoing process.
The international community has long struggled with the challenge of translating international law into actionable norms and practices in cyberspace. The conclusion of the United Nations Open-Ended Working Group (OEWG) on the security of and in the use of information and communications technologies 2021-2025 marks a vital milestone in that ongoing process.
- By Joanna Kulesza
- Comments: 0
- Views: 1,522
Increased Attacks Against ISP Networks
 Netscout recently released its latest Threat Intelligence Report that documents DDoS attacks in the second half of 2024. As has been the trend for many years, the largest target of DDoS attacks has been ISP networks. There were over 8.9 million DDoS attacks documented in the second half of last year, up 12.75% over the first half of the year.
Netscout recently released its latest Threat Intelligence Report that documents DDoS attacks in the second half of 2024. As has been the trend for many years, the largest target of DDoS attacks has been ISP networks. There were over 8.9 million DDoS attacks documented in the second half of last year, up 12.75% over the first half of the year.
- By Doug Dawson
- Comments: 0
- Views: 12,203
How Decades-Old Decisions Left U.S. Networks Vulnerable to Chinese Cyberintrusion
 It seems like there is more disturbing news every day about Chinese infiltration of our telecommunications networks. A recent headline said that nine large ISPs have now been infiltrated. Tom Wheeler, a previous Chairman of the FCC, recently wrote an article for the Brookings Institute that speculates that the ability of the Chinese to infiltrate our networks stems back to decisions made decades ago that have never been updated for the modern world of sophisticated hacking.
It seems like there is more disturbing news every day about Chinese infiltration of our telecommunications networks. A recent headline said that nine large ISPs have now been infiltrated. Tom Wheeler, a previous Chairman of the FCC, recently wrote an article for the Brookings Institute that speculates that the ability of the Chinese to infiltrate our networks stems back to decisions made decades ago that have never been updated for the modern world of sophisticated hacking.
- By Doug Dawson
- Comments: 0
- Views: 12,168
Has Your ISP Been Hacked? (Growing Concern Over AI-Driven Hacking)
 As if we didn't have a long enough list of problems to worry about, Lumen researchers at its Black Lotus Labs recently released a blog that said that it knows of three U.S. ISPs and one in India was hacked this summer. Lumen said the hackers took advantage of flaws in software provided by Versa Networks being used to manage wide-area networks.
As if we didn't have a long enough list of problems to worry about, Lumen researchers at its Black Lotus Labs recently released a blog that said that it knows of three U.S. ISPs and one in India was hacked this summer. Lumen said the hackers took advantage of flaws in software provided by Versa Networks being used to manage wide-area networks.
- By Doug Dawson
- Comments: 0
- Views: 12,852
The xz liblzma Vulnerability
 On 29 March 2024, an announcement was posted notifying the world that the Open-Source Software (OSS) package "xz-utils," which includes the xz data compression program and a library of software routines called "liblzma" and which is present in most Linux distributions, had been compromised. The insertion of the compromised code was done by "Jia Tan", the official maintainer of the xz-utils package.
On 29 March 2024, an announcement was posted notifying the world that the Open-Source Software (OSS) package "xz-utils," which includes the xz data compression program and a library of software routines called "liblzma" and which is present in most Linux distributions, had been compromised. The insertion of the compromised code was done by "Jia Tan", the official maintainer of the xz-utils package.
- By Paul Ebersman
- Comments: 0
- Views: 19,393
A Brief Primer on Anti-Satellite Warfare Tactics
 Satellites make it possible for governments to provide essential services, such as national defense, navigation, and weather forecasting. Private ventures use satellites to offer highly desired services that include video program distribution, telecommunications, and Internet access. The Russian launch of a satellite, with nuclear power and the likely ability to disable satellites, underscores how satellites are quite vulnerable to both natural and manmade ruin.
Satellites make it possible for governments to provide essential services, such as national defense, navigation, and weather forecasting. Private ventures use satellites to offer highly desired services that include video program distribution, telecommunications, and Internet access. The Russian launch of a satellite, with nuclear power and the likely ability to disable satellites, underscores how satellites are quite vulnerable to both natural and manmade ruin.
- By Rob Frieden
- Comments: 0
- Views: 17,570
Microsoft’s Size Means Malicious Cyber Actors Thrive
 Last month, the Russian state-sponsored hacking group "Midnight Blizzard" gained access to the email accounts of Microsoft leadership, even exfiltrating documents and messages. The group reportedly used a simple brute-force style attack to access a forgotten test account and then exploited the permissions on that account to access the emails of employees in the cybersecurity and legal teams.
Last month, the Russian state-sponsored hacking group "Midnight Blizzard" gained access to the email accounts of Microsoft leadership, even exfiltrating documents and messages. The group reportedly used a simple brute-force style attack to access a forgotten test account and then exploited the permissions on that account to access the emails of employees in the cybersecurity and legal teams.
- By George Rakis
- Comments: 0
- Views: 16,880
Challenges in Measuring DNS Abuse
 From the creation of DNSAI Compass ("Compass"), we knew that measuring DNS Abuse1 would be difficult and that it would be beneficial to anticipate the challenges we would encounter. With more than a year of published reports, we are sharing insights into one of the obstacles we have faced. One of our core principles is transparency and we've worked hard to provide this with our methodology.
From the creation of DNSAI Compass ("Compass"), we knew that measuring DNS Abuse1 would be difficult and that it would be beneficial to anticipate the challenges we would encounter. With more than a year of published reports, we are sharing insights into one of the obstacles we have faced. One of our core principles is transparency and we've worked hard to provide this with our methodology.
- By Rowena Schoo
- Comments: 0
- Views: 26,289
The Causes of Network Outages: Underlying Causes, Growing Threats and Industry Implications
 The Uptime Institute (UI) is an IT industry research firm best known for certifying that data centers meet industry standards. UI issues an annual report that analyzes the cause of data center outages. The causes for data center outages are relevant to the broadband industry because the same kinds of issues shut down switching hubs and Network Operations Centers.
The Uptime Institute (UI) is an IT industry research firm best known for certifying that data centers meet industry standards. UI issues an annual report that analyzes the cause of data center outages. The causes for data center outages are relevant to the broadband industry because the same kinds of issues shut down switching hubs and Network Operations Centers.
- By Doug Dawson
- Comments: 0
- Views: 23,050
How You Can Be Hijacked Without Actually Being Hacked
 Unsuspecting website visitors are often unaware when they have landed on a spoofed page or are re-directed to malware-hosting web servers designed to steal their sensitive data and information. This attack is known as subdomain hijacking, or subdomain takeover. A web user's private information is then traded on the dark web, and cybercriminals profit, further fueling the expansion of identity theft in the online world.
Unsuspecting website visitors are often unaware when they have landed on a spoofed page or are re-directed to malware-hosting web servers designed to steal their sensitive data and information. This attack is known as subdomain hijacking, or subdomain takeover. A web user's private information is then traded on the dark web, and cybercriminals profit, further fueling the expansion of identity theft in the online world.
- By Mark Flegg
- Comments: 0
- Views: 21,852
Risk vs Benefit: The Impact of Shorter 90-Day SSL Certificate Life Cycles
 In today's digital age, securing your website and ensuring your users' safety has never been more critical. Secure sockets layer (SSL) certificates are the go-to solution for securing websites by encrypting the data transmitted between web servers and browsers. Historically, SSL digital certificates could be valid for years, after which they had to be renewed or replaced.
In today's digital age, securing your website and ensuring your users' safety has never been more critical. Secure sockets layer (SSL) certificates are the go-to solution for securing websites by encrypting the data transmitted between web servers and browsers. Historically, SSL digital certificates could be valid for years, after which they had to be renewed or replaced.
- By Sue Watts
- Comments: 0
- Views: 22,192
OARC-40: Notes on the Recent DNS Operations, Analysis, and Research Centre Workshop
 OARC held a 2-day meeting in February, with presentations on various DNS topics. Here are some observations I picked up from the presentations in that meeting... In a world where every DNS name is DNSSEC-signed, and every DNS client validates all received DNS responses, we wouldn't necessarily have the problem of DNS spoofing. Even if we concede that universal use of DNSSEC is a long time off ...
OARC held a 2-day meeting in February, with presentations on various DNS topics. Here are some observations I picked up from the presentations in that meeting... In a world where every DNS name is DNSSEC-signed, and every DNS client validates all received DNS responses, we wouldn't necessarily have the problem of DNS spoofing. Even if we concede that universal use of DNSSEC is a long time off ...
- By Geoff Huston
- Comments: 0
- Views: 17,919
Brand Impersonation Online is a Multidimensional Cybersecurity Threat
 Brand impersonation happens much more often than people realize. In CSC's latest Domain Security Report, we found that 75% of domains for the Global 2000 that contained more than six characters from the brand names were not actually owned by the brands themselves. The intent of these fake domain registrations is to leverage the trust placed on the targeted brands to launch phishing attacks, other forms of digital brand abuse, or IP infringement...
Brand impersonation happens much more often than people realize. In CSC's latest Domain Security Report, we found that 75% of domains for the Global 2000 that contained more than six characters from the brand names were not actually owned by the brands themselves. The intent of these fake domain registrations is to leverage the trust placed on the targeted brands to launch phishing attacks, other forms of digital brand abuse, or IP infringement...
- By Sue Watts
- Comments: 0
- Views: 16,120
DNSAI Compass: Six Months of Measuring Phishing and Malware
 The DNS Abuse Institute recently published our sixth monthly report for our project to measure DNS Abuse: DNSAI Compass ('Compass'). Compass is an initiative of the DNS Abuse Institute to measure the use of the DNS for phishing and malware. The intention is to establish a credible source of metrics for addressing DNS Abuse. We hope this will enable focused conversations, and identify opportunities for improvement.
The DNS Abuse Institute recently published our sixth monthly report for our project to measure DNS Abuse: DNSAI Compass ('Compass'). Compass is an initiative of the DNS Abuse Institute to measure the use of the DNS for phishing and malware. The intention is to establish a credible source of metrics for addressing DNS Abuse. We hope this will enable focused conversations, and identify opportunities for improvement.
- By Rowena Schoo
- Comments: 0
- Views: 14,338
How to Avoid Insider Threats Such as the Latest New York Post Hacking
 New York Post has been "hacked" by an employee. To protect themselves from insider threats, companies can deploy zero trust and restrict access. On October 27, the New York Post published a string of racist and sexist articles on its website. Fabricated news about politicians, such as pieces concerning racist comments of a New York City mayor, has been headlining the publication.
New York Post has been "hacked" by an employee. To protect themselves from insider threats, companies can deploy zero trust and restrict access. On October 27, the New York Post published a string of racist and sexist articles on its website. Fabricated news about politicians, such as pieces concerning racist comments of a New York City mayor, has been headlining the publication.
- By Evan Morris
- Comments: 0
- Views: 16,216
News Briefs
 Cyberattacks Spur Boom in Insurance Demand Amid Rising Global Threats
Cyberattacks Spur Boom in Insurance Demand Amid Rising Global Threats
- May 28, 2025 10:53 AM PDT
- Comments: 0
 Massive Iberian Power Outage Raises Cybersecurity Questions
Massive Iberian Power Outage Raises Cybersecurity Questions
- Apr 29, 2025 11:32 AM PDT
- Comments: 0
 Massive Cyber Assault on X: Musk Hints at Foreign Involvement
Massive Cyber Assault on X: Musk Hints at Foreign Involvement
- Mar 10, 2025 2:21 PM PDT
- Comments: 0
 Chinese Hackers Exploit U.S. Telecom Systems, Eviction Efforts Lag
Chinese Hackers Exploit U.S. Telecom Systems, Eviction Efforts Lag
- Dec 04, 2024 8:12 AM PST
- Comments: 0
 Chinese Hackers Had Access to Canadian Government Systems for Years, Report Reveals
Chinese Hackers Had Access to Canadian Government Systems for Years, Report Reveals
- Nov 01, 2024 2:00 PM PDT
- Comments: 0
 Sudanese Nationals Charged in Global Cyberattack Campaign
Sudanese Nationals Charged in Global Cyberattack Campaign
- Oct 17, 2024 7:15 AM PDT
- Comments: 0
 Over 2 Million VPN Passwords Compromised by Malware Attacks
Over 2 Million VPN Passwords Compromised by Malware Attacks
- Sep 25, 2024 8:08 AM PDT
- Comments: 0
 FBI Takes Down China-Backed Botnet, Facilitates Ransomware Negotiations
FBI Takes Down China-Backed Botnet, Facilitates Ransomware Negotiations
- Sep 19, 2024 10:40 AM PDT
- Comments: 0
Rising Ransomware Threats and a Record-Breaking $75M Payout
- Jul 31, 2024 2:52 PM PDT
- Comments: 0
 Mystery Malware Takes Down 600,000 Windstream Routers in Coordinated Attack
Mystery Malware Takes Down 600,000 Windstream Routers in Coordinated Attack
- May 30, 2024 10:39 AM PDT
- Comments: 0
 Biden Administration Alerts Governors to Rising Cyber Threats on U.S. Water Systems
Biden Administration Alerts Governors to Rising Cyber Threats on U.S. Water Systems
- Mar 20, 2024 11:35 AM PDT
- Comments: 0
 Ransomware Crisis in U.S. Healthcare
Ransomware Crisis in U.S. Healthcare
- Mar 07, 2024 10:57 AM PST
- Comments: 0
 Global Law Enforcement Strikes Major Blow Against LockBit Ransomware Operation
Global Law Enforcement Strikes Major Blow Against LockBit Ransomware Operation
- Feb 22, 2024 10:49 AM PST
- Comments: 0
 Millions of Smart Toothbrushes Hijacked in Cyberattack on Swiss Firm
Millions of Smart Toothbrushes Hijacked in Cyberattack on Swiss Firm
- Feb 07, 2024 8:50 AM PST
- Comments: 1
 Ukraine’s Leading Mobile Operator Struck by War’s Largest Cyberattack
Ukraine’s Leading Mobile Operator Struck by War’s Largest Cyberattack
- Dec 13, 2023 10:49 AM PST
- Comments: 0
 Denmark Encounters Largest Cyber Attack on Its Critical Infrastructure to Date
Denmark Encounters Largest Cyber Attack on Its Critical Infrastructure to Date
- Nov 16, 2023 11:16 AM PST
- Comments: 0
 Activist Hackers Target Government Websites Amid Escalating Israel-Hamas War
Activist Hackers Target Government Websites Amid Escalating Israel-Hamas War
- Oct 10, 2023 8:33 AM PDT
- Comments: 0
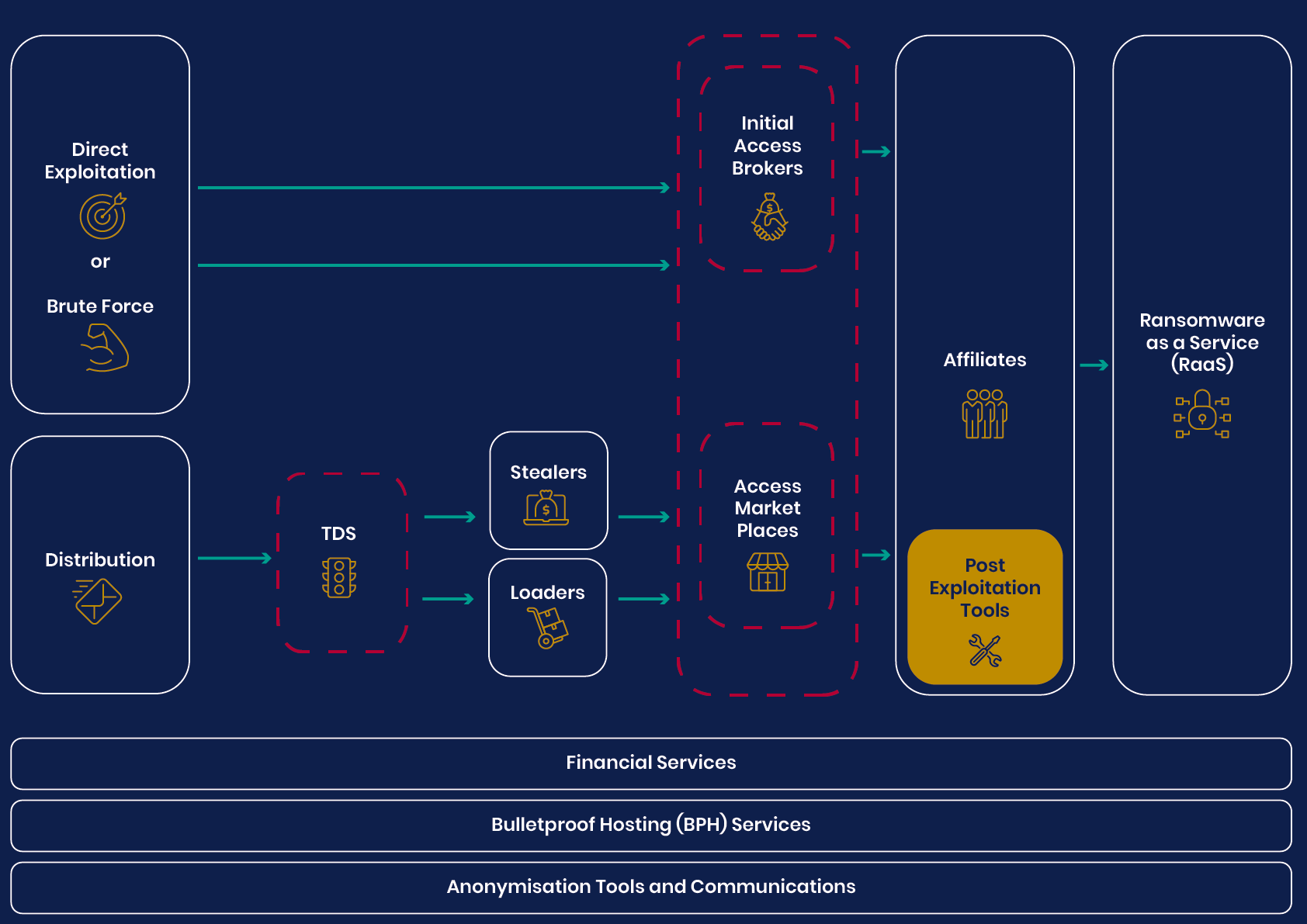 UK’s National Agencies Release White Paper on Evolving Cyber Crime Ecosystem
UK’s National Agencies Release White Paper on Evolving Cyber Crime Ecosystem
- Sep 11, 2023 11:25 AM PDT
- Comments: 0
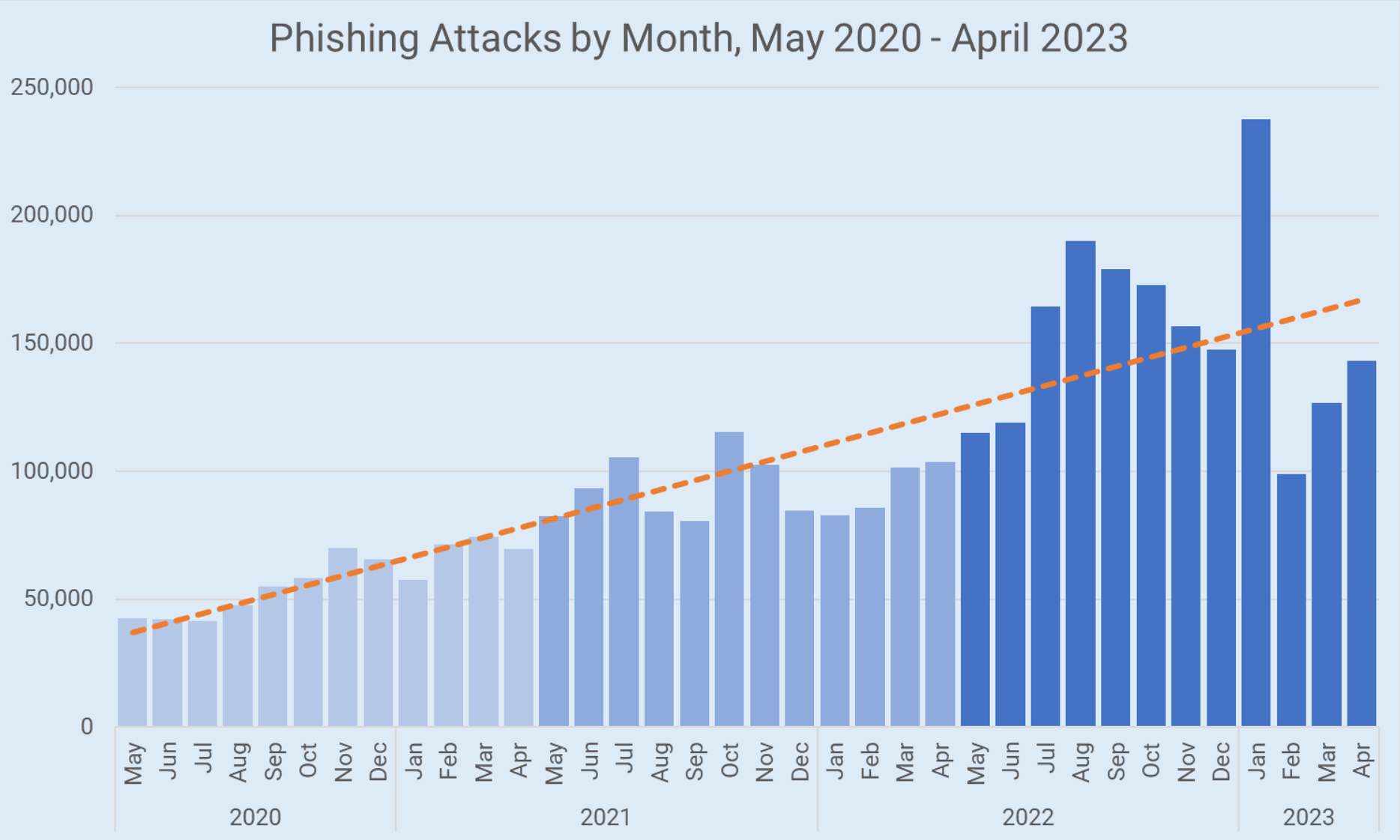 Phishing Attacks Surge Despite Increased Awareness, New Strategies Needed
Phishing Attacks Surge Despite Increased Awareness, New Strategies Needed
- Sep 03, 2023 8:54 AM PDT
- Comments: 0
The Rising Cost of Digital Theft and Espionage in Germany
- Sep 02, 2023 7:28 AM PDT
- Comments: 0
Most Viewed
Trench Warfare in the Age of The Laser-Guided Missile
- Jan 16, 2007
- Views: 528,797
Port 25 Blocking, or Fix SMTP and Leave Port 25 Alone for the Sake of Spam?
- Apr 17, 2005
- Views: 179,659
Where are DNS Root Servers? See them on Google Maps
- Sep 17, 2007
- Views: 124,440
Internet Governance Outlook 2017: Nationalistic Hierarchies vs. Multistakeholder Networks?
- Jan 06, 2017
- Views: 82,080
Examining Two Well-Known Attacks on VoIP
- Apr 05, 2006
- Views: 73,358
Most Commented
Port 25 Blocking, or Fix SMTP and Leave Port 25 Alone for the Sake of Spam?
- Comments: 31
- Views: 179,659
Most Abusive Domain Registrations are Preventable
- Comments: 25
- Views: 37,851
DNSSEC: Once More, With Feeling!
- Comments: 17
- Views: 68,342
Sorry, Not Sorry: WHOIS Data Must Remain Public
- Comments: 14
- Views: 34,405
An Attack on DNS is an Attack on the Internet
- Comments: 14
- Views: 50,766
Industry Updates
Down the DNS Funnel and into the Funnull Infrastructure
- By WhoisXML API
- Jul 11, 2025
Framing the AkiraBot Framework Under the DNS Lens
- By WhoisXML API
- Jul 10, 2025
Shining the DNS Spotlight on Lumma Stealer
- By WhoisXML API
- Jul 07, 2025
A DNS Examination of the Phishing Campaign Targeting Japanese Brokerage Firms
- By WhoisXML API
- Jun 30, 2025
A DNS Deep Dive into the LabHost PhaaS Infrastructure
- By WhoisXML API
- Jun 19, 2025
New MITRE ATT&CK Groups for 2025: A DNS Deep Dive
- By WhoisXML API
- Jun 10, 2025
Exploring the DNS Flipside of SideWinder
- By WhoisXML API
- May 30, 2025
Global Domain Activity Trends Seen in Q1 2025
- By WhoisXML API
- May 27, 2025
Attaxion Becomes the First EASM Platform to Integrate ENISA’s EU Vulnerability Database (EUVD)
- By Attaxion
- May 26, 2025
Unlocking the DNS Strongbox of BADBOX 2.0
- By WhoisXML API
- May 21, 2025
Unearthing the DNS Roots of the Latest Lotus Blossom Attack
- By WhoisXML API
- May 19, 2025
Detectify vs Intruder: External Attack Surface Management on a Budget
- By Attaxion
- May 14, 2025
Rounding Up the DNS Traces of RA World Ransomware
- By WhoisXML API
- May 12, 2025
Tempering Tax Season Troubles with DNS Intel
- By WhoisXML API
- May 06, 2025
Decrypting the Inner DNS Workings of EncryptHub
- By WhoisXML API
- May 02, 2025
Participants – Random Selection
View MoreSECTIONS: Home | Topics | Featured Blogs | News Briefs | Industry Updates | Community
TERMS OF USE: Codes of Conduct | Privacy Policy | Terms of Use
Copyright © 2002-2025 CircleID. All rights reserved unless where otherwise noted.
Local Time: Monday, July 14, 2025 03:34 PM PDT – Page Load: 0.2830 Sec.
