| CARVIEW |
Select Language
HTTP/2 308
server: envoy
x-frame-options: SAMEORIGIN
cache-control: public, s-maxage=86400, max-age=0, must-revalidate
location: https://www.slideshare.net/slideshow/binds-new-security-feature-dnsrpz-the-quotdns-firewallquot/9722792
refresh: 0;url=https://www.slideshare.net/slideshow/binds-new-security-feature-dnsrpz-the-quotdns-firewallquot/9722792
x-envoy-upstream-service-time: 228
p3p: CP="OTI DSP COR CUR ADM DEV PSD IVD CONo OUR IND"
x-content-type-options: nosniff
accept-ranges: bytes
date: Mon, 14 Jul 2025 17:22:55 GMT
via: 1.1 varnish
x-served-by: cache-bom4748-BOM
x-cache: MISS
x-cache-hits: 0
x-timer: S1752513775.448273,VS0,VE436
vary: accept-encoding, x-bot
set-cookie: browser_id=9c49e422-6911-44a0-88b7-30931be372d0; Domain=.slideshare.net; Path=/; Expires=Sat, 13 Jul 2030 17:22:55 GMT
strict-transport-security: max-age=63072000; includeSubDomains; preload
alt-svc: h3=":443";ma=86400,h3-29=":443";ma=86400,h3-27=":443";ma=86400
HTTP/2 200
content-type: text/html; charset=utf-8
server: envoy
x-frame-options: SAMEORIGIN
cache-control: public, s-maxage=86400, max-age=0, must-revalidate
x-powered-by: Next.js
etag: "14u70a8h4bfhf27"
content-encoding: gzip
x-envoy-upstream-service-time: 398
p3p: CP="OTI DSP COR CUR ADM DEV PSD IVD CONo OUR IND"
x-content-type-options: nosniff
accept-ranges: bytes
age: 0
date: Mon, 14 Jul 2025 17:22:57 GMT
via: 1.1 varnish
x-served-by: cache-bom4748-BOM
x-cache: MISS
x-cache-hits: 0
x-timer: S1752513776.898654,VS0,VE1244
vary: accept-encoding, x-bot
strict-transport-security: max-age=63072000; includeSubDomains; preload
alt-svc: h3=":443";ma=86400,h3-29=":443";ma=86400,h3-27=":443";ma=86400
content-length: 113101
BIND’s New Security Feature: DNSRPZ - the "DNS Firewall" | PDF 




































BIND’s New Security Feature: DNSRPZ - the "DNS Firewall"
10 likes12,265 views
The document introduces the DNS Response Policy Zone (DNSRPZ), a new feature by ISC aimed at enhancing DNS security by allowing real-time collaboration between DNS data producers and consumers to mitigate cyber threats. It outlines the operational roles of ISC in deploying and supporting DNSRPZ, details its structure and functions, and emphasizes the importance of taking proactive measures against malicious actors leveraging the DNS infrastructure. Furthermore, it discusses potential uses of DNSRPZ in enterprise and service provider environments to combat threats like malware and phishing.
1 of 66
Downloaded 323 times


































































More Related Content
What's hot (20)
PPTX
Uygulamali Sizma Testi (Pentest) Egitimi Sunumu - 1BTRisk Bilgi Güvenliği ve BT Yönetişim HizmetleriUygulamali Sizma Testi (Pentest) Egitimi Sunumu - 1BTRisk Bilgi Güvenliği ve BT Yönetişim Hizmetleri
Viewers also liked (20)
Ad
Similar to BIND’s New Security Feature: DNSRPZ - the "DNS Firewall" (20)
PDF
ION Mumbai - Shailesh Gupta: Business Case for IPv6 and DNSSECDeploy360 Programme (Internet Society)PDF
ION San Diego - DNSSEC Deployment Panel Introductory SlidesDeploy360 Programme (Internet Society)ION Mumbai - Shailesh Gupta: Business Case for IPv6 and DNSSECDeploy360 Programme (Internet Society)
Ad
BIND’s New Security Feature: DNSRPZ - the "DNS Firewall"
- 1. The image cannot be displayed. Your computer may not have enough memory to open the image, or the image may have been corrupted. Restart your computer, and then open the file again. If the red x still appears, you may have to delete the image and then insert it again. DNS Response Policy Zone (DNSRPZ) BIND’s New Security Feature: the "DNS Firewall" Barry Raveendran Greene & Vernon Schryver bgreene@isc.org Version 1.1
- 2. Logistics • This presentation can be downloaded from the Webinar recording and from ISC’s Knowledge Base: https://deepthought.isc.org • ISC updates, presentations, and materials can be followed on: Facebook - https://www.facebook.com/InternetSystemsConsortium Twitter - ISCdotORG Linkedin - https://www.linkedin.com/company/internet-systems-consortium RSS via our Website
- 3. Our Goal – Take Back DNS DNS works as well for the bad guys (criminals, spammers, spies) as for respectable citizens. The bad guys are taking better advantage of DNS's resiliency and distributed autonomy. Something has got to be done! ISC is acting: Act I – Massive Passive DNS Deployment Act II - DNSRPZ
- 4. Agenda • The DNSRPZ Quick Talk • Why do we need DNSRPZ? • More Details • DNSRPZ Providers
- 5. Gratitude • Paul Vixie and Vernon Schryver for all the heavy lifting to make DNSRPZ happen. • ISC’s BIND Engineering Team – for integrating this new feature so quickly. • Eric Ziegast - my partner in explaining DNSRPZ to people. • For the new DNSRPZ Providers: Simon Forster forster@spamteq.com Arnie Bjorklund arnieb@securityzones.net Rod Rasmussen rod.rasmussen@internetidentity.com • Johanna Mansor who helped put this together so quickly.
- 7. DNS Response Policy Zone (DNS RPZ) • DNS RPZ is policy information inside a specially constructed DNS zone. • This enables DNS reputation data producers and consumers to cooperate in the application of such policy to real time DNS responses. • DNS RPZ turns the recursive DNS server into a security hammer … Provide the same capabilities of an anti-spam DNSBL (DNS Block List, ne RBL) and RHSBL (Right Hand Side Block List)…. … with greater degrees of scaling and speed.
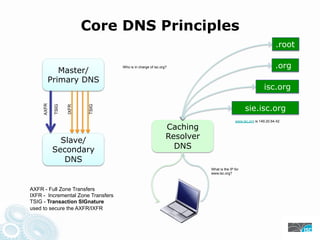
- 8. Core DNS Principles .root .org Master/ Who is in charge of isc.org? Primary DNS isc.org sie.isc.org AXFR TSIG TSIG IXFR www.isc.org is 149.20.64.42 Caching Resolver Slave/ Secondary DNS DNS What is the IP for www.isc.org? AXFR - Full Zone Transfers IXFR - Incremental Zone Transfers TSIG - Transaction SIGnature used to secure the AXFR/IXFR
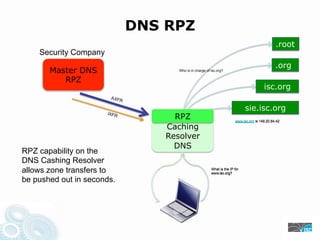
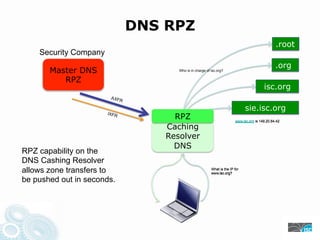
- 9. DNS RPZ .root Security Company .org Master DNS Who is in charge of isc.org? RPZ isc.org AXF R sie.isc.org IXFR RPZ www.isc.org is 149.20.64.42 Caching Resolver DNS RPZ capability on the DNS Cashing Resolver allows zone transfers to What is the IP for www.isc.org? be pushed out in seconds.
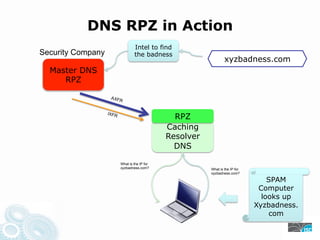
- 10. DNS RPZ in Action Intel to find Security Company the badness xyzbadness.com Master DNS RPZ AXF R IXFR RPZ Caching Resolver DNS What is the IP for xyzbadness.com? What is the IP for xyzbadness.com? SPAM Computer looks up Xyzbadness. com
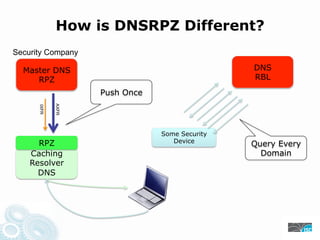
- 11. How is DNSRPZ Different? Security Company Master DNS DNS RPZ RBL Push Once AXFR IXFR Some Security RPZ Device Query Every Caching Domain Resolver DNS
- 12. Demo - before
- 13. Demo - after
- 14. What it looks like
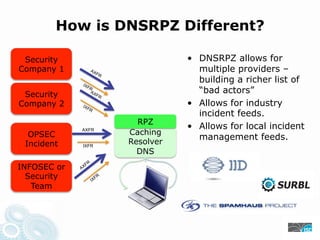
- 15. How is DNSRPZ Different? Security • DNSRPZ allows for Company 1 multiple providers – building a richer list of Security “bad actors” Company 2 • Allows for industry incident feeds. RPZ • Allows for local incident OPSEC AXFR Caching management feeds. Incident IXFR Resolver DNS INFOSEC or Security Team
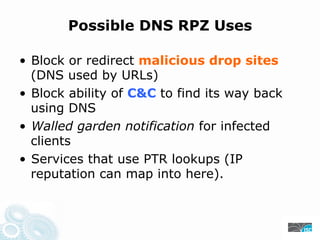
- 16. Possible DNS RPZ Uses • Block or redirect malicious drop sites (DNS used by URLs) • Block ability of C&C to find its way back using DNS • Walled garden notification for infected clients • Services that use PTR lookups (IP reputation can map into here).
- 17. Possible Uses Examples • Enterprise networks can us it to stop infections – and let NOC know something is wrong. • Hosting Provider can use it to block infected customer host – and let NOC know something is wrong. • Service Providers – can use it to protect customers AND notify customer AND let the help desk know customers might be infected.
- 18. DNSRPZ Getting the Word out • There was a healthy amount of pre-announced to operational security community to build a ecosystem. • With BIND 9.8.1, we have a solid version for operators and networks to migrate and try DNSRPZ. • ISC’s role is to now get the word out. The next wave of deployments would determine the utility of this security widget.
- 19. ISC’s Role with DNS RPZ • ISC has three roles with DNS RPZ as a new “hammer” in our security toolkit: Code and Functionality in BIND & working with all DNS Recursive Resolver Software Vendors to insure everyone is adopting the same formats. Work with all potential Black List Providers. Work with Operators on DNS RPZ Deployment. • ISC will NOT be providing any black list capacities. Our role is to help design, build, and deploy the “hammer” as a new tool in our security toolkit.
- 21. Links while you are thinking … • Discussion List • https://lists.isc.org/mailman/listinfo/dnsrpz-interest • Taking back the DNS, Paul Vixie, 29th July 2010 • https://www.isc.org/community/blog/201007/taking- back-dns-0 • Google “taking back the dns” • Draft Specification • ftp://ftp.isc.org/isc/dnsrpz/isc-tn-2010-1.txt • BIND 9.8.1 • ftp://ftp.isc.org/isc/bind9/9.8.1/
- 22. Why We Need DNSRPZ?
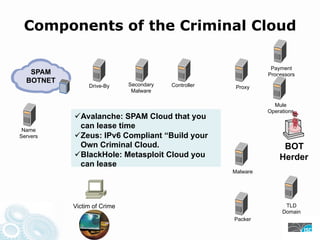
- 23. Components of the Criminal Cloud Payment SPAM Processors BOTNET Drive-By Secondary Controller Proxy Malware Mule Operations Avalanche: SPAM Cloud that you Name can lease time Servers Zeus: IPv6 Compliant “Build your Own Criminal Cloud. BOT BlackHole: Metasploit Cloud you Herder can lease Malware Victim of Crime TLD Domain Packer
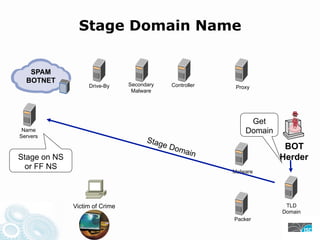
- 24. Stage Domain Name SPAM BOTNET Drive-By Secondary Controller Proxy Malware Get Name Domain Servers Stag e Do BOT main Stage on NS Herder or FF NS Malware Victim of Crime TLD Domain Packer
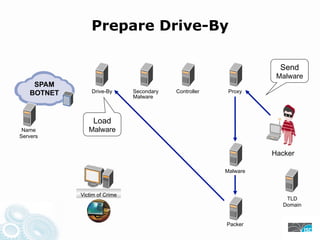
- 25. Prepare Drive-By Send Malware SPAM BOTNET Drive-By Secondary Controller Proxy Malware Load Name Malware Servers Hacker Malware Victim of Crime TLD Domain Packer
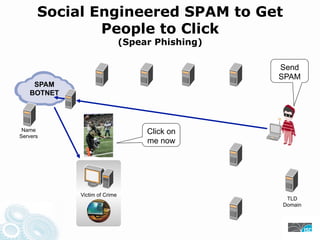
- 26. Social Engineered SPAM to Get People to Click (Spear Phishing) Send SPAM SPAM BOTNET Drive-By Secondary Controller Proxy Malware Name Click on Servers me now Hacker Malware Victim of Crime TLD Domain Packer
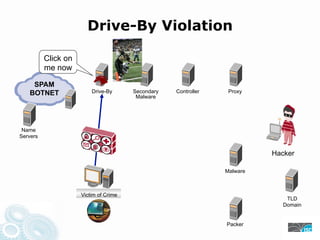
- 27. Drive-By Violation Click on me now SPAM BOTNET Drive-By Secondary Controller Proxy Malware Name Servers Hacker Malware Victim of Crime TLD Domain Packer
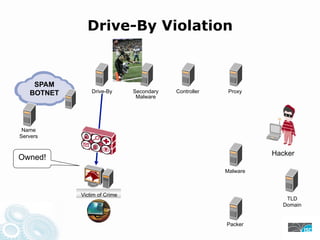
- 28. Drive-By Violation SPAM BOTNET Drive-By Secondary Controller Proxy Malware Name Servers Hacker Owned! Malware Victim of Crime TLD Domain Packer
- 29. Poison Anti-Virus Updates SPAM BOTNET Drive-By Secondary Controller Proxy Malware Name Servers Poison the anti-virus updates Hacker All updates to 127.0.0.1 Anti-Virus Malware Vendor Victim of Crime TLD Domain Packer
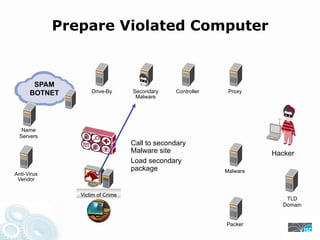
- 30. Prepare Violated Computer SPAM BOTNET Drive-By Secondary Controller Proxy Malware Name Servers Call to secondary Malware site Hacker Load secondary package Malware Anti-Virus Vendor Victim of Crime TLD Domain Packer
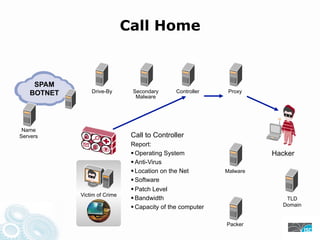
- 31. Call Home SPAM BOTNET Drive-By Secondary Controller Proxy Malware Name Servers Call to Controller Report: Operating System Hacker Anti-Virus Location on the Net Malware Software Patch Level Victim of Crime Bandwidth TLD Capacity of the computer Domain Packer
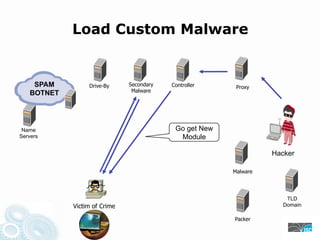
- 32. Load Custom Malware SPAM Drive-By Secondary Controller Proxy Malware BOTNET Name Go get New Servers Module Hacker Malware TLD Victim of Crime Domain Packer
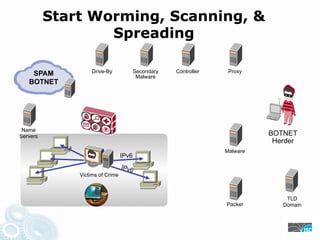
- 33. Start Worming, Scanning, & Spreading SPAM Drive-By Secondary Controller Proxy Malware BOTNET Name Servers BOTNET Herder Malware IPv6 IPv6 Victims of Crime TLD Packer Domain
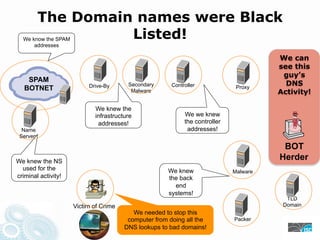
- 34. The Domain names were Black We know the SPAMListed! addresses We can see this guy’s SPAM Drive-By Secondary Controller DNS BOTNET Proxy Malware Activity! We knew the infrastructure We we knew addresses! the controller Name addresses! Servers BOT We knew the NS Herder used for the We knew Malware criminal activity! the back end systems! TLD Victim of Crime Domain We needed to stop this computer from doing all the Packer DNS lookups to bad domains!
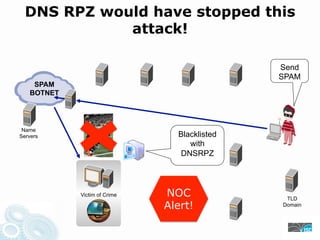
- 35. DNS RPZ would have stopped this attack! Send SPAM SPAM BOTNET Drive-By Secondary Controller Proxy Malware Name Servers Blacklisted with DNSRPZ Hacker Malware Victim of Crime NOC TLD Alert! Domain Packer
- 36. We need to look “out of the Box” • Put things in context – this illustrate was real. The computer was up to date with all the patches. The anti-virus was up to date. The users getting hit with MEBROOT/Torpig were all using Firefox and Noscipt Some of the users were security people. The network was locked down with firewalls, IDPs, and all the other BCP recommended. The zero day hit was orchestrated from the criminals known domains!
- 38. During the Questions ….. • How do you get support for DNSRPZ? • Today, that is with BIND: Public Benefit support through the community: https://lists.isc.org/mailman/listinfo/dnsrpz-interest Public Benefit support through the ISC Knowledge Base: https://deepthought.isc.org BIND Software Support Package • Yes! ISC does Internet Critical Software Support Services. • https://www.isc.org/getbindsupport for a BIND upgrade package
- 40. Original Problem Statement • DNS is a decentralized system offering complete distributed autonomy. The relationships between operators and content owners are both tenuous and resilient. • The split registry/registrar/registrant model insulates all parties from responsibility, so the global DNS lacks accountability. Complaints are ineffective, even with provable crime/losses. • This resiliency and unaccountability benefits the bad actors committing cyber-crime.
- 41. Historical Context • DNS is not unique in its unaccountability. Most Internet systems (mail, blogs, I-M) are similar. • In e-mail it's extremely common to subscribe to an DNSBL (realtime blackhole list) in order to reject messages from known-bad sources. • Features similar to DNSBL exist for DNS in proprietary products (Nominum) and services (OpenDNS). • RPZ (ISC Response Policy Zone) is an open standard for DNSBL-like features in the DNS.
- 42. DNS IND (&T) IETF DNSIND working group (mid 1990's): (I)ncremental zone transfer – RFC 1995 (N)otification of zone changes – RFC 1996 (D)ynamic update of zone content – RFC 2136 (T)ransaction signatures (TSIG) – RFC 2845 Pre-IND DNS zone changes had long latency, heavy bandwidth, and low trust – so, high cost Post-IND DNS zone changes are immediate, with small deltas and good forward secrecy
- 43. RPZ History • RPZ 1.0 released as patches to BIND9 in 2010: • Rule-based system, triggered on query name/ type • Rule-forced outcomes: Return a fake alias (CNAME), for walled gardens Return a fake NXDOMAIN, to blackout the name Return a fake answer of the type being queried Protect the name against subsequent policy triggers • Subscription model: recursive name servers would become stealth servers for one or more RPZs. • Rules/outcomes encoded as RPZ zone content.
- 44. DNS RPZ .root Security Company .org Master DNS Who is in charge of isc.org? RPZ isc.org AXF R sie.isc.org IXFR RPZ www.isc.org is 149.20.64.42 Caching Resolver DNS RPZ capability on the DNS Cashing Resolver allows zone transfers to What is the IP for www.isc.org? be pushed out in seconds.
- 45. RPZ Content Examples (1) • If rpz.net is a response policy zone and example.com is a name to be blacked out: example.com.rpz.net CNAME . • If all subdomains of example.com are to be aliased to a local walled garden: *.example.com.rpz.net CNAME wg.isc.org • If www.example.com/A should be redirected: www.example.com A 198.168.6.66
- 46. RPZ Content Examples (2) • If www.partner.com is to be protected from any policy action by any subsequent RPZ: www.partner.com.rpz.net CNAME www.partner.com • If www.example.com is to appear to be empty: www.example.com.rpz.net CNAME *. • If a A RRs in 192.168.1.0/24 are to be replaced with a local walled garden address: 24.0.1.168.192.rpz-ip.rpz.net A 192.168.6.66
- 47. RPZ Content Examples (3) • If AAAA RR's in 2001:500:2f::/48 ought to cause fake NXDOMAIN responses, except 2001:500:2f::f which is to be returned as normal: 128.f.zz.2f.500.2001.rpz-ip.rpz.net CNAME *. 48.zz.2f.500.2001.rpz-ip.rpz.net CNAME . • Note: “zz” in this context means “::”.
- 48. Lessons Learned From RPZ 1.0 • Sometimes the trigger has to be answer-based E.g., if the A or AAAA RR is within a CIDR block E.g., if the NS name or address is poisoned • Sometimes the subscriber wants to import the triggers but locally specify the policy outcome E.g., import a list of bad names, but decide locally whether to blackout or alias those names • We have implemented some of these features in RPZ Format 2, released in BIND 9.8.0.
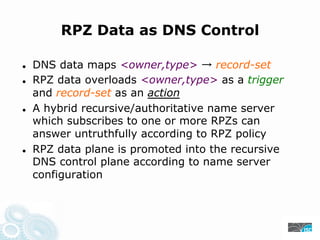
- 49. RPZ Data as DNS Control DNS data maps <owner,type> record-set RPZ data overloads <owner,type> as a trigger and record-set as an action A hybrid recursive/authoritative name server which subscribes to one or more RPZs can answer untruthfully according to RPZ policy RPZ data plane is promoted into the recursive DNS control plane according to name server configuration
- 50. RPZ Format 1 (in 2010) Triggers: Actions: Q-name (all types) Exemption Q-name, Q-type Force NXDOMAIN Force empty answer Force CNAME answer Force specific answer
- 51. RPZ Format 2 (in 2011) New Triggers: New Actions: Answer in netblock None Name server name Name server address in netblock
- 52. Subscriber Configuration in BIND9 options { // other stuff response-policy { zone "dns-policy1.vix.com"; zone "dns-policy2.vix.com" policy given; zone "dns-policy3.vix.com" policy NO-OP; zone "dns-policy4.vix.com" policy NXDOMAIN; zone "dns-policy5.vix.com" policy NODATA; zone "dns-policy6.vix.com" policy CNAME walled-garden.isp.net; }; }; zone “dns-policy1.vix.com” { type slave; masters { 192.168.1.123; }; // note: TSIG would probably be used in a production environment }; // and similar for the other rpz zones
- 53. Producer/Consumer Model in RPZ • Producers can use RFC 2136 “UPDATE” to maintain their zone, or just periodically regenerate it and use “ixfr-from-differences” to tell BIND to compute deltas. • Producers will use IXFR for efficient zone delta transmission, and TSIG for protection of RPZ data and authenticity of producer/consumer endpoints. • Result: low cost, low bandwidth, low latency, and strong data protection.
- 54. Possible Good • Specialization of labor: security experts can produce robust and targeted patterns for use by customer DNS recursive name servers. • Competition: many security experts, many name server implementers (not just BIND!), and a global market of potential customers. • Effect on crime: a domain or IP address used only for evil will not remain usable even if its registrant, registrar, registry, or ISP never suspends or terminates it.
- 55. Possible Harm • Governments could use RPZ to enforce laws about censorship, since it is an open standard. • Some RPZ data sources will inevitably be politically, racially, or religiously motivated (“all Christian web sites” or “all Muslim web sites”). • As with all reputation systems, the systemic effect on DNS will be to make it less reliable and harder to diagnose or characterize. • We hope these effects will be more pronounced on bad actors than on the rest of us.
- 57. During the Questions ….. • Download & save for later reading the Protect IP Paper: • Security and Other Technical Concerns Raised by the DNS Filtering Requirements in the Protect IP Bill. https://infojustice.org/archives/3469 • Security Week Article: https://www.securityweek.com/
- 58. DNSRPZ Providers
- 60. ActiveTrust® Resolver RPZ • Focused on enterprise threats Malware distribution and communications Phishing, including spear-phishing Data exfiltration • Constantly updated with fresh information Market-leading detection of phishing and malware sites Criminal infrastructure analysis using passive DNS Malware reverse-engineering including DGAs Detection and analysis of anomalous DNS requests • Updated every 15 minutes • Optional TrapTrace™ redirection and analysis service to determine who, what, when for blocked connections Detailed info on threats on your network from IID Threat Intel Team • More info at internetidentity.com
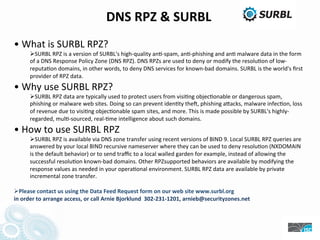
- 61. DNS RPZ & SURBL • What is SURBL RPZ? SURBL RPZ is a version of SURBL's high-‐quality an>-‐spam, an>-‐phishing and an> malware data in the form of a DNS Response Policy Zone (DNS RPZ). DNS RPZs are used to deny or modify the resolu>on of low-‐ reputa>on domains, in other words, to deny DNS services for known-‐bad domains. SURBL is the world's first provider of RPZ data. • Why use SURBL RPZ? SURBL RPZ data are typically used to protect users from visi>ng objec>onable or dangerous spam, phishing or malware web sites. Doing so can prevent iden>ty theN, phishing aOacks, malware infec>on, loss of revenue due to visi>ng objec>onable spam sites, and more. This is made possible by SURBL's highly-‐ regarded, mul>-‐sourced, real-‐>me intelligence about such domains. • How to use SURBL RPZ SURBL RPZ is available via DNS zone transfer using recent versions of BIND 9. Local SURBL RPZ queries are answered by your local BIND recursive nameserver where they can be used to deny resolu>on (NXDOMAIN is the default behavior) or to send traffic to a local walled garden for example, instead of allowing the successful resolu>on known-‐bad domains. Other RPZsupported behaviors are available by modifying the response values as needed in your opera>onal environment. SURBL RPZ data are available by private incremental zone transfer. Please contact us using the Data Feed Request form on our web site www.surbl.org in order to arrange access, or call Arnie Bjorklund 302-‐231-‐1201, arnieb@securityzones.net
- 63. Don’t get Caught Off Guard with Old BIND! • Get Professional Support to help you upgrade BIND! https://www.isc.org/getbindsupport • Special Offer Software Support & Consulting Deal! Take advantage of this special deal that combines 6 months of Basic Support & 8 hours of Expert Consulting to get your organization started with BIND support, have enough support time to get your systems upgraded, and convince management to budget for critical DNS infrastructure support. • Webinar Special Discount! ISC will E-mail all participants after the webinar. If you did not get or cannot wait, E-mail to sales@isc.org
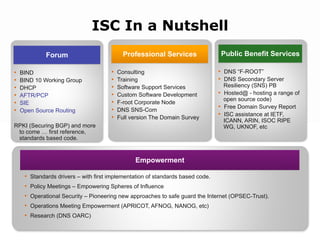
- 64. ISC In a Nutshell Forum Professional Services Public Benefit Services • BIND • Consulting • DNS “F-ROOT” • BIND 10 Working Group • Training • DNS Secondary Server • DHCP • Software Support Services Resiliency (SNS) PB • AFTR/PCP • Custom Software Development • Hosted@ - hosting a range of open source code) • SIE • F-root Corporate Node • • Free Domain Survey Report • Open Source Routing DNS SNS-Com • Full version The Domain Survey • ISC assistance at IETF, ICANN, ARIN, ISOC RIPE RPKI (Securing BGP) and more WG, UKNOF, etc to come … first reference, standards based code. Empowerment • Standards drivers – with first implementation of standards based code. • Policy Meetings – Empowering Spheres of Influence • Operational Security – Pioneering new approaches to safe guard the Internet (OPSEC-Trust). • Operations Meeting Empowerment (APRICOT, AFNOG, NANOG, etc) • Research (DNS OARC)
- 65. New from ISC
- 66. ISC Technology Leadership for the Common Good

